Little was known about the ciphers of the Unabomber, a highly intelligent serial killer, until the FBI published a detailed description last year. Here’s a summary.
Ted Kaczynski, also known as the “Unabomber”, is one of most notorious criminals in US history. Being a gifted mathematician trained at Harvard and Berkeley, Kaczynski renounced a promising scientific career and moved to a cabin in Montana, in 1971. Between 1978 and 1995, he engaged in a nationwide bombing campaign against people involved with modern technology, mailing or planting bombs, ultimately killing a total of three people and injuring 23 others.
Before Kaczynski’s identity was known, the FBI titled the perpetrator “UNABOM” (UNiversity & Airline BOMber), since his bombs often targeted universities and airlines, which resulted in the media calling him “Unabomber”. The search for this serial murderer was the most expensive manhunt in US history.
Kaczynski finally was caught after he had sent a lengthy treatise (“Unabomber Manifesto”) to The Washington Post and The New York Times. The two newspapers published the manifesto, which led to his sister-in-law and his brother recognizing his writing style and opinions. Kaczynski was arrested in 1996 and sentenced to life in prison with no possibility of parole.
Kaczynski’s encrypted journals
When FBI agents searched Kaczynski’s cabin after his arrest, they seized tens of thousands of hand-written pages. Among these journals were several that were encrypted using cipher systems of Kaczynski’s own design.
Of course, Kaczynski’s journals and his encryption methods raised interest in the crypto community. However, there was no official publication about them for almost two decades. Like in dozens of other criminal cases involving encryption, police was very reluctant in publishing information about the cipher systems. As it seems, some of Kaczynski’s cipher material somehow made it to the internet, but it is unclear what exactly was published by whom.
When UK crypto blogger Nick Pelling reported about the Unabomber cipher journal in 2013, the situation was quite confusing. I encountered the same problem when I carried out some research about the Unabomber ciphers myself. Here is an article about my search (in German), and here’s my (now outdated) summary in English.
Finally, an FBI publication
The speculations about Ted Kaczynski’s encryption activities finally came to an end, when in 2015 the FBI published an article titled “Kaczynski’s Ciphers” in the scientific magazine, Cryptologia. It was written by Jeanne Anderson, cryptanalyst in the Cryptanalysis and Racketeering Records Unit (CRRU) of the FBI.
According to this article, Kaczynski used two distinct encryption systems (Code # I and Code # II). The FBI cryptanalyzed both of them based on instructions and keys found alongside the journals. It seems unlikely that FBI cryptanalysists had been successful without these aids. As Kaczynski did not intend to pass encrypted messages to somebody else, there was no need to share the keys or the rules of the system.
Kaczynski’s Code # I
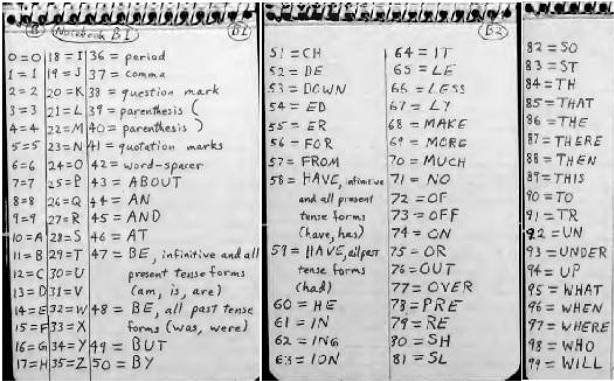
The more complex cipher system, Code # I, is based on a nomenclator (a substitution table listing a number for each letter of the alphabet and for common words). This nomenclator is named “list of meanings”.
In the first step, the encipherer encrypts the cleartext with this nomenclator. E.g. CRYPTO becomes 42 60 70 58 57. Now the following key table is needed:
The encipherer extracts a number sequence from this table (this is step 2 of the method). The starting point and the direction are part of the key. E.g., if the starting point is the beginning of line 5 and the direction is from left to right, the number sequence is 27, 8, 8, 0, 35, 44, … In cryptography, such a sequence is named “key stream”. Step 2 may be referred to as key stream generation.
In the third step, the text created with the nomenclator is subtracted from the key stream (modulo 90):
27 8 8 0 35 32 30 20 22 37 -------------- 85 68 78 58 88
Step 3 represents the application of a One Time Pad (OTP). It is unusual that cleartext and key stream subtracted instead of added, but from a cryptographer’s point of view this does not make a big difference. An OTP-like encryption based on a deteministicly generated key stream is also referred to a “stream cipher”.
All in all, Code # I is a combination of a nomenclator and a stream cipher.
In order to make this system more secure, Kaczynski introduced various safeguards, including the use of intentional misspellings, encryption errors, meaningless punctuation, nonsense words, and Spanish and German text intermixed with English plaintext and ciphertext. Kaczynski also chose to omit and add word breaks at random and use meaningless numbers (nulls).
There are a few details I omitted in my description (e.g. the way the key is placed in front of the cipher text). For a complete specification please refer to the Cryptologia publication.
The following image shows a decryption process (this means that addition instead of substraction is used). The ciphertext is “72 24 74 …”. It was encrypted with the key stream “47 74 64 …”. Adding the two sequences modulo 90 results in “29 8 48 60 …”, which is translated by the nomenclator to “I WILL HAVE …”.
Code # II
Code # II is similar to Code # I, but less complex. Again, a nomenclator is used:
Like Code # I, Code # II subtracts the numbers generated with the nomenclator from a key stream. This key stream is generated by adding the number sequences given in two different notebooks.
Conclusion
Kaczyinski’s approach of combining a nomenclator with a stream cipher is nothing outstanding from a cryptographer’s point of view. Modern encryption methods, like AES or RSA, are by magnitudes more secure. However, Kaczyinski’s methods are among the most complex and most secure manual encryption systems (i.e., they were applied without a computer). Encrypting a whole journal in such a complex code is certainly unusual.
Jeanne Anderson, in her article, comes to the following conclusion: “His [Kaczyinski’s] systems, while complex and theoretically successful in concealing messages from someone with no knowledge of the systems, would be impractical for use operationally. They require many key documents to encipher and decipher, and their complexity would rule out broad usage. Kaczynski, however, was able to successfully use these systems as a personal encryption method to secure his outlet for his emotions and personal thoughts. He utilized these systems to both express and conceal his frustrations and anger with society. His writings gave details about his attacks as well as his satisfaction with his crimes.”
Follow @KlausSchmeh
Further reading: Who can make sense of a child murderer’s encrypted notes?







Kommentare (12)