Substituting letter pairs (bigrams) is an encryption method that was already known in the 16th century. Is it still secure today?
To develop an encryption method that only requires pen and paper is a difficult task. Many ciphers of this kind, e.g. the Caesar cipher, the Vigenère cipher or the Playfair cipher have proven insecure. Among the best concepts known to me are the double columnar transposition and the One Time Pad. Book ciphers, encryption with a Rubik’s cube and encryption with a card deck (Solitaire) are interesting methods, too, as they only require unsuspicious everyday objects.
There’s another encryption method which only requires pen and paper but is still not easy to break: the bigram substitution. A bigram is a letter pair, e.g., CG, HE, JS or QW. The number of letter bigrams in the Latin alphabet is 26×26=676, ranging from AA to ZZ. A bigram substitution replaces each letter pair with another one (or with a symbol or with a number between 1 and 676). In order to use a bigram substitution, we need a substitution table with 676 entries.
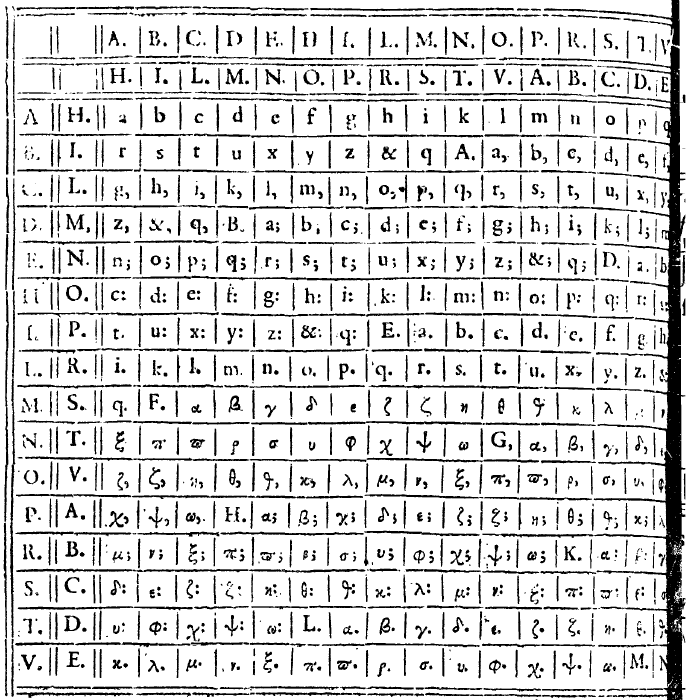
Porta’s bigram substitution
The oldest bigram substitution I am a ware of is described in the marvelous book De Furtivis Literarum Notis written by 16th century cryptologist Giambattista della Porta. Porta uses a 20 letter alphabet. He therefore needs a substitution table with 400 entries. Here it is:
As can be seen, Porta substitutes each letter pair with a symbol. He must have been quite inventive to come up with 400 different symbols. For instance, the bigram IA is replaced with a symbol that looks like an X. The bigram VO is substituted with something resembling an O. Here’s a ciphertext Porta mentions in his book (the solution is available here).
Vigenère’s bigram substitution
Blaise de Vigenère invented a bigram substitution, too. Here is his table:
Vigenère replaces each bigram with a single letter or a letter followed by a dot, colon or semicolon. E.g., LM is substituted with “r.”.
RSHA bigram substitution
The following bigram substitution, which is described in David Kahn’s book The Codebreakers, was used by the Nazi authority Reichssicherheitshauptamt (RSHA):
How secure is a bigram substution?
It is clear that a bigram substitution can be broken with a bigram frequency analysis. Here are the most frequent English bigrams (according to Wikipedia):
th 1.52 en 0.55 ng 0.18 he 1.28 ed 0.53 of 0.16 in 0.94 to 0.52 al 0.09 er 0.94 it 0.50 de 0.09 an 0.82 ou 0.50 se 0.08 re 0.68 ea 0.47 le 0.08 nd 0.63 hi 0.46 sa 0.06 at 0.59 is 0.46 si 0.05 on 0.57 or 0.43 ar 0.04 nt 0.56 ti 0.34 ve 0.04 ha 0.56 as 0.33 ra 0.04 es 0.56 te 0.27 ld 0.02 st 0.55 et 0.19 ur 0.02
However, a frequency analysis will not be successful if the ciphertext is short enough. On the other hand, it doesn’t make much sense to use a bigram substitution for a ciphertext of, say, 400 letters because the One Time Pad is more efficient in such a case (dealing with a 400 letter One Time Pad key is certainly easier than using a substitution table with 676 entries).
For this reason, the bigram substitution is especially interesting for messages that contain between, say, 1500 and 5000 letters. The main question is if the bigram substitution is secure enough for messages of such a length or if a frequency analysis can break it. In order to answer this question, I have created two bigram challenges, one with a 2500 letter message and one with a 5000 letter message.
The bigram 2500 challenge
The following ciphertext encrypts an English cleartext with 2500 letters. Each number (between 0 and 675) represents a bigram:
205 211 230 674 450 545 445 541 221 216 323 434 274 611 46 212 387 201 83 450 134 257 674 545 496 209 608 394 90 255 103 151 191 650 151 266 565 646 189 7 255 299 674 290 626 7 193 249 281 231 486 179 302 450 107 674 151 368 483 230 461 631 568 665 302 597 205 577 462 312 214 21 290 626 7 193 249 281 577 503 545 674 316 302 106 434 445 305 626 642 648 282 170 368 671 642 264 445 580 383 97 179 65 306 7 266 70 365 179 191 450 107 595 54 396 189 603 364 650 580 205 230 322 517 295 234 496 238 255 364 196 545 503 628 229 381 148 478 316 153 122 580 248 381 445 602 214 385 478 205 368 630 384 674 264 597 29 96 11 600 257 631 580 189 473 189 597 205 324 103 222 221 189 26 70 292 375 381 562 42 431 302 106 434 445 305 617 299 29 423 205 67 642 580 265 374 214 272 260 405 26 264 600 11 450 562 42 32 238 234 388 1 46 229 208 229 66 153 657 198 122 580 577 70 292 375 381 4 373 523 205 381 212 122 387 124 131 523 205 368 66 122 299 602 214 248 234 189 170 368 70 292 375 602 580 282 122 248 396 450 362 481 230 461 202 312 597 14 302 106 434 445 305 539 299 119 214 373 205 324 457 368 381 212 218 153 502 65 247 545 595 602 355 463 177 582 179 485 36 450 290 626 7 193 249 46 169 404 119 7 151 447 105 375 416 153 5 211 648 116 368 202 312 597 66 322 517 295 11 265 393 248 21 205 634 665 151 238 218 97 447 452 580 577 545 302 597 381 674 151 597 566 221 478 450 42 577 565 85 499 229 7 413 221 365 211 490 342 317 530 177 135 302 106 434 445 305 481 70 373 327 323 170 368 205 577 261 6 463 110 178 292 211 205 577 266 565 646 189 39 665 151 238 122 90 131 396 370 257 603 496 46 611 368 439 191 675 374 251 207 565 450 396 205 577 194 265 595 151 327 615 85 606 24 191 290 626 7 193 249 46 169 221 216 10 665 151 342 138 84 230 255 103 450 107 674 205 11 221 302 106 434 445 305 481 381 212 122 235 11 387 201 384 233 103 384 597 7 205 674 287 642 514 299 131 191 496 481 209 238 218 154 191 212 663 385 42 478 205 375 602 387 602 214 396 205 179 211 501 449 475 122 608 461 450 107 674 364 608 572 212 189 29 87 214 288 191 650 151 266 565 646 189 490 302 106 434 445 305 481 7 323 45 450 435 368 450 107 595 580 603 306 447 179 191 214 11 205 209 447 83 450 435 368 478 205 375 602 387 602 580 205 221 447 316 46 631 521 530 557 46 194 131 191 496 481 209 238 218 646 191 503 496 375 7 154 191 387 159 212 663 503 496 375 608 131 191 496 481 209 238 218 445 151 209 324 375 608 196 131 205 366 103 151 209 324 375 608 131 191 496 481 209 238 496 191 450 7 323 299 674 45 333 447 577 384 385 282 445 131 191 496 481 209 238 218 154 191 212 663 385 42 478 205 375 602 387 602 214 396 205 221 46 261 122 490 189 70 292 375 490 486 512 179 174 445 123 549 214 597 66 461 248 381 445 602 214 42 387 201 230 212 274 545 562 42 32 373 342 215 333 179 595 387 461 215 333 179 595 127 302 106 434 445 305 422 46 194 131 191 496 481 209 238 122 299 127 486 512 577 191 562 42 342 212 248 229 580 211 11 565 57 289 642 7 503 541 191 381 94 597 248 385 42 450 461 299 212 248 229 580 230 461 205 221 46 70 289 672 11 523 205 447 11 565 57 221 46 194 131 191 496 481 209 238 135 189 70 292 375 490 486 512 179 174 445 123 189 316 153 122 580 36 490 189 218 251 674 545 496 248 381 445 602 214 205 221 342 167 375 29 674 355 214 450 70 373 327 323 577 265 391 368 234 562 42 191 42 191 445 450 290 179 368 249 595 225 381 552 539 201 373 431 59 11 205 619 28 141 151 26 151 368 384 214 205 221 46 631 449 450 107 674 301 539 449 353 42 238 496 191 212 663 141 151 26 387 194 582 383 557 486 261 602 580 517 342 167 375 29 260 7 455 674 355 214 450 176 481 559 230 57 205 209 87 324 368 422 46 631 664 373 45 42 671 229 597 373 191 386 368 306 87 481 642 503 496 642 167 211 577 255 116 85 447 539 496 191 215 333 179 595 127 59 179 191 212 663 342 85 7 674 364 450 290 179 552 640 66 449 11 552 1 46 212 577 413 384 113 646 191 212 248 229 580 211 11 565 57 289 642 7 503 124 373 16 191 387 159 189 134 191 545 595 675 211 255 384 7 344 178 205 577 552 591 52 234 388 481 387 159 478 205 375 602 387 602 214 577 202 597 21 674 503 333 375 364 582 603 255 491 27 214 234 496 611 191 674 205 211 230 674 214 21 584 567 211 501 449 475 122 521 597 387 450 396 615 237 375 647 26 642 557 191 394 597 108 122 521 205 324 189 483 324 375 7 154 191 450 290 179 552 591 29 521 503 628 672 387 381 4 292 211 205 530 11 151 191 674 447 221 447 306 591 381 164 176 211 230 615 237 375 647 26 642 557 447 306 189 316 191 394 597 108 122 521 214 21 413 11 52 234 388 481 552 591 287 532 307 387 159 299 674 396 381 494 230 672 450 134 46 611 377 597 387 450 396 59 52 234 388 481 212 663 478 205 375 602 387 602 214 205 221 46 261 450 299 70 233 209 619 28 287 374 84 28 113 646 191 212 248 229 580 211 11 565 57 289 642 7 503 541 191 381 94 597 248 385 42 255 384 151 191 261 582 481 552 617 45 248 21 70 365 103 384 59 264 331 42 248
Can a reader break it?
The bigram 5000 challenge
The following ciphertext encrypts an english cleartext with 5000 letters. Each number (between 0 and 675) represents a bigram (the substitution table is different from the one used in the bigram 2500 challenge):
205 355 133 441 417 449 183 204 43 547 263 188 556 355 194 631 110 646 30 68 181 163 654 241 438 561 18 39 418 590 449 628 496 392 556 667 659 490 229 642 251 418 562 449 128 194 557 360 493 230 374 288 510 499 484 157 452 75 194 654 157 452 75 241 438 561 18 39 418 590 449 628 496 36 204 30 665 76 157 263 222 178 180 355 459 62 160 43 355 136 157 178 590 194 80 499 236 362 110 161 418 19 526 418 194 355 62 12 233 510 282 632 429 454 72 317 178 580 37 418 574 292 394 184 564 496 241 656 194 46 438 67 46 194 355 672 20 418 19 178 549 76 9 564 39 418 366 194 265 30 292 184 656 194 438 403 441 510 579 556 667 659 427 30 314 656 194 496 407 115 256 444 205 355 79 592 76 241 83 493 612 373 605 169 292 265 517 509 418 19 194 205 201 158 79 62 37 418 659 69 517 538 71 564 128 194 557 360 493 230 313 157 620 641 574 292 394 184 128 194 449 107 205 496 394 68 62 309 158 265 30 184 76 241 83 493 612 373 335 76 189 95 510 62 37 175 404 150 556 418 43 308 499 115 630 580 620 641 46 510 158 265 30 184 656 282 355 17 523 9 157 452 75 592 338 394 579 76 579 567 667 414 452 30 150 381 219 0 317 481 438 418 19 314 663 282 628 30 425 403 646 517 659 239 76 656 510 158 265 30 184 128 194 449 24 592 15 0 564 504 418 376 612 158 265 30 184 579 335 338 221 39 604 308 201 499 107 208 556 46 194 499 493 93 205 201 158 499 454 628 496 213 300 557 46 411 499 537 27 46 141 355 231 641 115 450 510 97 580 425 646 30 314 499 107 208 556 259 67 454 366 194 265 30 493 30 314 4 641 205 355 201 300 338 43 627 46 314 663 455 324 658 394 549 43 79 73 499 316 411 592 15 0 454 510 190 441 79 454 178 141 438 459 308 499 107 208 556 46 579 335 632 591 438 30 314 510 499 107 208 556 654 404 4 70 555 201 158 79 604 355 115 575 4 30 411 459 520 233 43 374 288 194 631 75 656 194 672 549 43 79 669 392 517 659 239 76 493 93 496 641 355 76 575 186 161 201 425 403 76 600 580 665 323 496 173 258 592 30 68 158 265 30 184 579 335 510 499 107 208 556 438 510 192 241 510 213 356 79 667 556 241 510 204 68 194 672 549 43 79 206 450 288 438 67 46 499 107 208 556 46 493 43 478 205 201 158 499 454 128 194 194 99 642 656 499 107 208 556 46 335 76 303 43 156 313 258 458 570 39 418 632 509 46 17 574 213 70 659 169 493 30 314 408 12 612 73 269 318 591 233 576 483 39 418 141 438 459 308 634 324 468 499 672 421 336 207 556 646 194 355 157 201 425 403 76 617 201 160 578 449 517 418 499 107 208 556 46 335 76 303 43 350 241 67 110 252 314 592 429 355 672 69 517 362 392 517 659 239 76 150 233 525 612 350 79 454 534 252 665 324 493 516 366 194 265 30 493 30 314 46 110 292 201 663 564 194 566 456 304 656 672 532 509 281 265 421 534 659 450 335 560 39 418 632 186 534 332 355 231 641 115 523 233 43 79 36 303 43 534 516 659 72 68 313 546 252 482 68 282 580 520 641 115 7 509 178 583 360 307 580 252 441 64 628 493 93 496 556 418 43 308 499 454 632 186 534 374 80 592 107 499 115 248 313 632 186 534 169 450 309 510 620 632 656 46 317 314 201 313 92 83 427 30 314 17 252 441 64 628 628 496 532 79 115 392 403 141 438 421 656 499 107 208 556 438 201 425 403 30 314 499 107 208 556 46 4 70 192 265 525 612 148 444 248 313 549 493 549 150 150 455 324 656 499 107 208 556 438 355 30 169 493 76 150 392 517 659 239 76 620 324 459 308 499 496 641 335 7 628 189 490 189 43 418 125 514 631 83 75 374 458 573 313 244 510 192 194 449 69 178 574 150 189 204 335 90 355 30 169 493 76 128 194 449 335 546 481 308 506 133 418 317 650 499 309 438 288 46 374 288 157 355 30 169 493 30 314 366 194 313 79 507 391 444 205 355 194 592 31 7 656 499 107 208 556 13 510 190 564 593 269 318 226 403 669 580 36 564 3 549 358 672 85 628 127 373 76 485 314 355 496 17 248 313 194 592 592 194 499 79 592 178 509 288 570 308 499 454 178 564 521 330 496 493 564 205 355 507 355 30 169 493 76 213 75 646 30 314 564 300 189 30 314 499 107 208 556 438 355 30 169 493 76 230 555 39 478 46 178 233 584 43 418 493 516 229 659 68 110 252 314 201 296 499 115 340 452 241 632 205 265 421 194 14 0 317 634 394 184 656 241 510 204 68 194 654 229 659 68 394 520 30 303 656 194 454 509 281 265 674 309 194 355 459 282 628 184 592 201 183 525 575 313 496 575 418 499 107 208 556 438 355 30 169 493 76 201 381 178 233 579 517 659 239 76 150 233 189 20 183 642 532 309 564 504 452 141 580 620 641 510 85 510 192 556 64 296 454 205 265 449 421 158 39 418 493 516 534 324 418 642 233 67 314 150 517 659 239 76 163 175 404 628 39 604 308 201 663 632 429 158 454 467 194 438 628 189 421 336 37 418 153 404 672 194 355 192 317 650 454 467 194 438 628 584 193 580 72 549 575 269 253 355 392 381 373 76 485 72 537 392 556 418 43 308 499 454 241 510 75 403 392 517 659 239 76 194 499 592 632 591 438 76 189 450 613 4 571 507 510 192 233 520 44 454 178 67 157 233 549 43 658 552 438 366 642 79 17 659 204 392 394 184 510 579 556 418 43 308 79 507 510 192 632 429 265 535 454 265 30 201 20 233 499 454 564 350 241 360 404 564 15 6 631 375 133 418 75 620 641 628 669 517 659 239 76 17 37 418 493 516 667 304 355 510 356 452 241 258 570 308 79 110 9 592 317 314 150 233 291 510 76 579 83 531 429 499 514 573 404 178 4 7 36 499 107 208 556 46 510 575 547 641 159 630 355 231 641 115 450 178 194 654 4 671 362 83 188 36 303 43 454 564 194 80 355 665 83 85 628 65 153 496 450 656 300 454 308 499 454 659 69 421 665 392 213 303 43 510 549 560 175 454 564 642 154 549 20 659 634 68 620 324 459 308 499 46 632 46 265 178 43 418 493 516 496 241 499 107 208 556 438 510 314 663 192 233 300 449 337 669 642 126 308 14 580 72 549 251 79 475 418 258 570 308 79 263 450 265 178 37 418 667 304 355 510 356 79 468 454 308 499 454 110 9 592 317 314 204 70 93 669 520 549 646 90 136 313 194 592 110 9 592 317 314 194 46 355 72 620 632 429 158 355 4 163 547 399 663 534 646 7 194 14 355 231 641 115 248 313 194 259 408 564 46 20 67 672 230 510 549 584 70 659 248 313 3 574 493 516 70 659 169 578 36 620 324 459 308 499 39 4 30 141 580 70 93 133 418 158 493 516 229 659 68 366 194 265 30 493 30 314 656 194 46 355 72 620 632 429 158 355 79 592 15 496 324 4 619 233 549 43 658 381 317 650 454 467 194 438 628 579 233 3 233 642 425 233 194 510 194 0 631 375 604 580 72 549 617 658 510 366 194 265 30 493 76 85 4 531 336 667 247 418 106 313 45 7 667 180 573 499 107 208 556 46 628 438 233 499 454 229 659 68 194 205 201 158 79 604 355 115 584 37 418 584 425 303 43 592 258 570 316 75 65 336 444 205 265 18 265 510 499 107 208 556 672 141 580 72 549 65 669 195 628 619 628 189 30 17 668 449 252 672 7 14 265 549 43 374 288 79 79 592 194 355 566 313 14 0 317 481 39 4 178 75 642 126 308 14 580 72 549 193 67 642 150 392 517 659 239 76 178 510 591 418 252 355 72 620 18 265 194 592 499 107 208 556 672 411 159 79 201 663 317 650 454 194 355 438 672 70 161 510 192 350 233 194 499 194 438 314 76 43 592 263 44 438 30 37 418 233 592 523 189 204 335 381 159 392 249 233 194 355 438 672 72 68 642 126 308 14 580 72 549 232 67 178 107 408 517 418 17 309 620 656 194 496 517 659 239 76 510 575 418 263 484 222 308 499 115 560 4 531 336 667 525 70 232 510 190 564 92 517 659 239 76 317 7 14 265 549 43 663 374 288 157 628 189 17 37 265 523 24 46 483 578 36 67 79 665 506 163 418 493 516 667 304 355 493 531 591 189 233 407 663 263 43 580 403 55 438 631 332 355 17 392 394 248 313 665 30 314 18 308 25 404 192 230 628 454 128 194 591 418 252 355 72 620 163 418 233 534 233 3 549 358 499 107 208 556 654 510 627 654 265 30 17 325 510 296 454 564 366 642 161 265 107 308 571 133 452 317 671 67 454 314 632 509 46 642 317 340 452 241 499 107 208 556 46 313 67 642 324 454 163 499 654 265 421 628 14 580 72 549 65 133 418 493 516 79 642 154 656 263 309 642 194 592 282 632 547 241 592 3 233 263 188 36 253 4 43 418 263 560 14 178 369 233 336 480 183 499 564 92 517 659 239 76 671 556 79 233 7 355 195 313 454 499 282 580 76 407 115 392 7 391 159 418 516 80 233 631 332 659 338 135 18 64 496 392 517 659 239 76 493 93 573 659 517 265 178 67 665 324 493 516 229 659 68 194 14 580 229 407 115 630 580 620 641 194 566 5 616 591 265 30 201 656 194 592 76 241 523 183 166 592 314 663 555 316 403 481 672 520 198 163 564 464 628 127 493 93 99 54 499 454 499 107 208 556 46 136 76 633 672 68 592 350 454 534 252 613 4 457 163 592 350 510 620 632 429 592 115 83 68 67 110 292 201 632 509 46 317 318 438 46 150 590 194 592 632 509 46 195 408 76 450 309 39 4 178 375 669 107 408 76 579 517 659 239 76 632 429 158 355 665 106 659 76 510 499 107 208 556 631 43 547 493 516 241 285 510 499 107 208 556 14 580 72 549 659 163 604 308 201 663 107 159 213 233 65 669 642 126 308 14 580 72 549 305 313 564 163 510 620 510 80 429 355 95 265 226 313 335 183 646 523 375 564 46 667 55 523 516 355 178 157 452 205 496 408 355 620 43 659 493 517 659 239 76 665 392 213 303 43 79 592 408 12 612 73 46 483 454 178 642 455 646 76 642 126 308 14 580 72 549 252 374 288 499 107 208 556 14 580 72 549 252 510 463 313 631 70 324 288 255 39 418 484 556 12 612 206 363 592 208 36 564 313 549 324 0 420 457 324 350 241 282 580 620 641 194 362 256 510 620 557 538 496 556 418 43 308 499 115 630 580 178 263 36 646 571 411 46 159 75 549 646 592 499 94 362 455 324 604 580 178 263 567 4 30 150 399 394 454 192 171 362 392 241 285 493 516 222 549 324 418 263 43 580 183 169 421 667 304 355 72 67 665 324 493 516 231 532 36 571 233 67 355 72 620 632 429 158 355 510 579 392 517 659 239 76 632 429 158 355 213 75 646 612 133 452 141 580 178 263 90 288 634 75 150 408 355 620 43 355 454 282 632 547 241 128 194 194 46 355 72 620 632 429 158 355 510 575 418 219 355 499 313 4 72 68 523 189 233 407 263 531 438 30 314 128 194 194 46 373 76 485
Can a reader break this challenge?
Follow @KlausSchmeh
Further reading: How my readers solved the Fleissner challenge
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/





Kommentare (20)