The M-209 is a small and robust encryption machine used by the US Army in World War II. Although several cryptologists have developed powerful methods to break the M-209, one series of messages is still unsolved.
Click here for the complete top 50 list
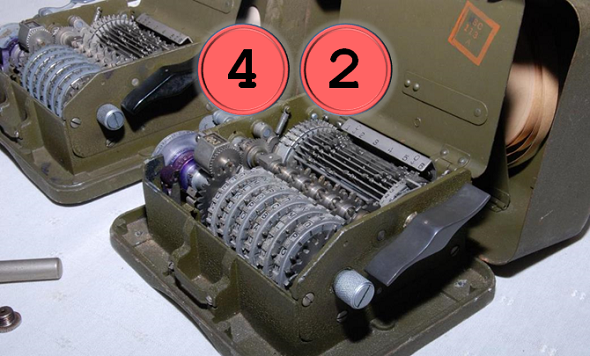
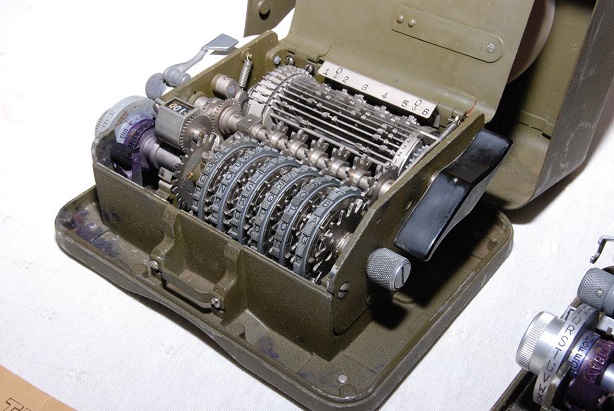
In every larger collection of historical cipher devices you can expect to find an M-209. The M-209 is a portable, mechanical encryption machine used by the US military primarily in World War II, though it remained in active use through the Korean War. About 140,000 copies were built, which makes the M-209 the probably most manufactured cipher machine in history (the photographs shown here were provied to me by Marc Simons and Paul Reuvers from the Cryptomuseum).
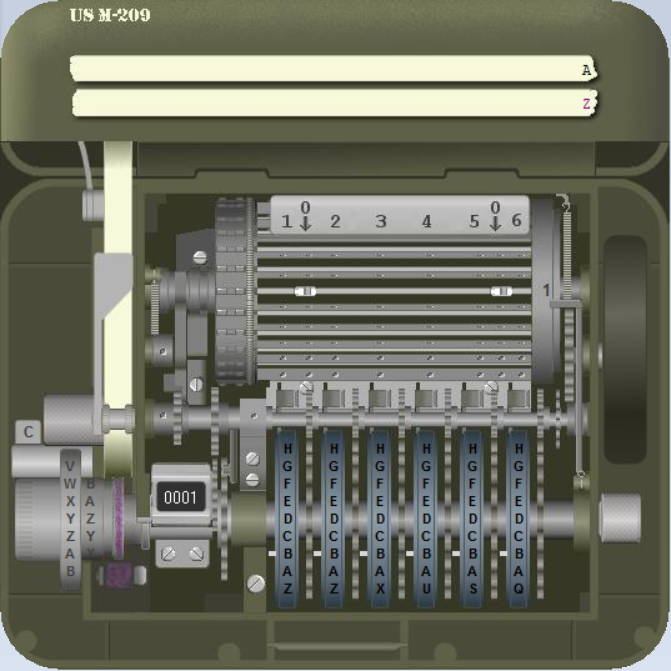
The M-209 was used as a field cipher. For this purpose, it was designed to be small, robust, and lightweight. Instead of a keyboard (like the Enigma) it contained a letter wheel. The operator had to set a certain cleartext letter and press a lever, which made the machine print the corresponding ciphertext letter on a thin sheet of paper.
The M-209 uses three different keys (the recipient needs all of them to decrypt a message):
- Wheels: The position of the six wheels at the front is a key (this key was usually different for every message encrypted). Wheels #1, #2, #3, #4, #5, and #6 are labeled with 26, 25, 23, 21, 19, and 17 letters, respectively.
- Pins: Every wheel has a pin for every letter, which can be active or inactive. Activating or deactivating a notch is only possible when the cover is open.
- Lugs: Inside the machine there’s a rotating cage with 27 bars. Each bar in the cage has two movable lugs. Each lug may be set against any of the six wheels or set to a neutral position.
A great M-209 simulator was programmed by Dirk Rijmenants.
Security of the M-209
The M-209 is not as secure as the Enigma or other well-known encryption machines. The cryptologists of the US Army, which belonged to the best of their time, probably knew this. However, as the M-209 was only used as a field cipher, it had not to be unbreakable. Typically, M-209 encrypted messages contained things like position reports, material orders, weather reports or warnings, which usually lost their value within days or even hours. It was therefore sufficient to make decipherment difficult, while absolute security was not needed.
In fact, already in World War II several German crypto units independently from each other found ways to break the M-209. In 2004 I had the chance to talk to a German WW2 codebreaker named Reinold Weber, who reported about a codebreaking machine that was constructed by German specialists in order to decipher M-209 messages.
Even decades after WW2, when the M-209 was long out of use, crypto experts developed new attacks on this machine. E.g., in the late 1970s, Jim Reeds, Robert Morris, and Unix inventor Dennis Ritchie introduced a ciphertext-only method for recovering keys from Hagelin M-209 messages.
In 1977 US cryptologist Wayne G. Barker published a book named Cryptanalysis of the Hagelin Cryptograph. It described a method to break the M-209. This book includes a number of M-209 challenges. Another series of 40 challenges with increasing difficulty
was published by Jean-Francois Bouchaudy on his M-209 Challenge website. This series starts with 12 challenges referenced on the main page. The remaining 28 problems are referred to as Bonus Challenges.
Recently, George Lasry became interested in the M-209. George is a great codebreaker specialising in historical cryptograms that were encrypted in a known cipher (i.e., the challenge is to find the key). His favorite codebreaking technique is hill climbing. George has broken many different historical ciphers with hill climbing algorithms.




Kommentare (11)