In the third step, the text created with the nomenclator is subtracted from the key stream (modulo 90):
27 8 8 0 35 32 30 20 22 37 -------------- 85 68 78 58 88
Step 3 represents the application of a One Time Pad (OTP). It is unusual that cleartext and key stream subtracted instead of added, but from a cryptographer’s point of view this does not make a big difference. An OTP-like encryption based on a deteministicly generated key stream is also referred to a “stream cipher”.
All in all, Code # I is a combination of a nomenclator and a stream cipher.
In order to make this system more secure, Kaczynski introduced various safeguards, including the use of intentional misspellings, encryption errors, meaningless punctuation, nonsense words, and Spanish and German text intermixed with English plaintext and ciphertext. Kaczynski also chose to omit and add word breaks at random and use meaningless numbers (nulls).
There are a few details I omitted in my description (e.g. the way the key is placed in front of the cipher text). For a complete specification please refer to the Cryptologia publication.
The following image shows a decryption process (this means that addition instead of substraction is used). The ciphertext is “72 24 74 …”. It was encrypted with the key stream “47 74 64 …”. Adding the two sequences modulo 90 results in “29 8 48 60 …”, which is translated by the nomenclator to “I WILL HAVE …”.
Code # II
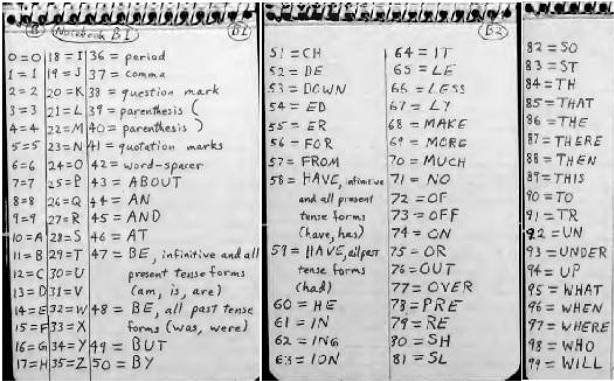
Code # II is similar to Code # I, but less complex. Again, a nomenclator is used:
Like Code # I, Code # II subtracts the numbers generated with the nomenclator from a key stream. This key stream is generated by adding the number sequences given in two different notebooks.
Conclusion
Kaczyinski’s approach of combining a nomenclator with a stream cipher is nothing outstanding from a cryptographer’s point of view. Modern encryption methods, like AES or RSA, are by magnitudes more secure. However, Kaczyinski’s methods are among the most complex and most secure manual encryption systems (i.e., they were applied without a computer). Encrypting a whole journal in such a complex code is certainly unusual.
Jeanne Anderson, in her article, comes to the following conclusion: “His [Kaczyinski’s] systems, while complex and theoretically successful in concealing messages from someone with no knowledge of the systems, would be impractical for use operationally. They require many key documents to encipher and decipher, and their complexity would rule out broad usage. Kaczynski, however, was able to successfully use these systems as a personal encryption method to secure his outlet for his emotions and personal thoughts. He utilized these systems to both express and conceal his frustrations and anger with society. His writings gave details about his attacks as well as his satisfaction with his crimes.”
Follow @KlausSchmeh
Further reading: Who can make sense of a child murderer’s encrypted notes?




Kommentare (12)