William Friedman, one of the most notable cryptologists in history, used a 16th century stegnography system to hide messages in pictures. Some of his codes are hard to decrypt. Maybe a reader can help.
Some people believe that Francis Bacon (1561-1626) was the real author of the works attributed to William Shakespeare. Many Baconians, as these people are called, even say that Bacon coded his name in these works using steganograpic techniques. While serious Shakespeare research has long proven the Baconians wrong, it is true that Francis Bacon invented an interesting steganographic method – the Bacon cipher.
The Bacon cipher
The purpose of the Bacon cipher is to hide a message in an arbitrary text or picture (“anything can be made to signify anything”). In order to use the Bacon cipher with a text, we need two different typesets (“a type” and “b type”). In the following I will use ordinary letters as type a and italic bold letters as type b. With these two types we can encode all letters of the alphabet (Bacon used a 25 letter alphabet) as follows:
A: SONNE B : SONNE C: SONNE D: SONNE
E: SONNE F : SONNE G: SONNE H: SONNE
I: SONNE K : SONNE L: SONNE M: SONNE
N: SONNE O : SONNE P: SONNE Q: SONNE
R: SONNE S : SONNE T: SONNE U: SONNE
W: SONNE X : SONNE Y: SONNE Z: SONNE
With the Bacon cipher the word CRYPTOLOG is coded as follows: “This is an ordinary Text containing a hidden message!”
The Bacon cipher can be easily modified in order to use it in a picture. E.g., a short line represents type a, a long line type b. The Bacon cipher is one of the earliest binary codes in history, predating the Morse code by over 300 years and the ASCII code by over 400 years. Here’s an English version of Bacon’s book chapter about it.
William Friedman’s sunflower code
Let’s now turn to William Friedman (1891-1969). Friedman is considered the most successful codebreaker in history. In his career, which spanned almost four decades, he solved over 1,000 encryption codes, including the Japanese WW2 cipher machine “Purple”. He also occupied himself with the Voynich manuscript and the Shakespeare Bacon debate.
William Friedman liked the Bacon cipher. He mentions it in several of his publications. For his students and readers he created a number of interesting examples.
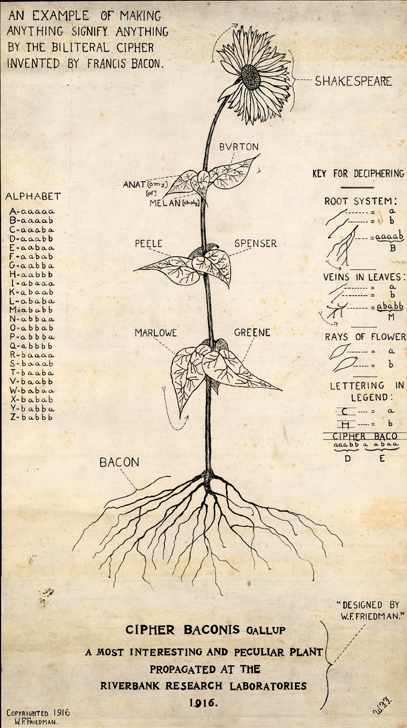
Before his career as a cryptologist, William Friedman had attended Cornell University and received a degree in genetics. It therefore comes to no surprise that he used a picture of a sunflower to hide a number of Bacon-coded words (taken from a blog post written by William H. Sherman, :
Can you find the coded letters? In fact, Friedman has hidden nine words in this sunflower. Here’s the explanation:
There are words (Shakespeare, Marlowe, Bacon, …) hidden in the blossom, in the leaves and in the root. But honestly, even with this explanation I can’t reproduce all the coded expressions. Maybe a reader can come up with a better explanation.
A castle with a coded message
It gets even worse when we look at the following picture of a castle (taken from the book A Friedman Legacy published by the NSA):
The shaded and unshaded stones code the following Bacon message:
My business is to write prescriptions
And then to see my doses staken
But now I find I spend my time
Endeavoring to out-Bacon Bacon
It’s not easy to decode the message, even if one knows it is there.
A musical code
And finally, here’s a coded message in a piece of music (taken from the William H. Sherman blog post):
Sherman writes the following about this sheet:
Only the tell-tale caption at the bottom, “An example of making anything signify anything,” tips us off to the Baconian cipher it contains. This time Friedman left no key, but once we notice that some of the notes have small gaps in them (b-types), and some are whole (a-types), it does not take long to extract the secret message: “ENEMY ADVANCING RIGHT / WE MARCH AT DAYBREAK.
Honestly, I can’t find the gaps that distinguish the a types from the b types. If you can, please let me know.
Follow @KlausSchmeh
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/
Further reading: How my readers solved a tricky cryptogram from the 19th century







Kommentare (5)