The crypto number table is a simple, yet far from trivial cipher. Can you break a cryptogram I have created with this method?
Designing a purely manual cipher (i.e., one that can be computed by hand) has proven a difficult problem. Most designs are either too complicated for practical use or insecure (some are even both). Almost all manual ciphers that were developed in the pre-computer era can be broken today with a computer. Although manual encryption algorithms have lost importance with the advent of cheap computers, they are still an active field of research.
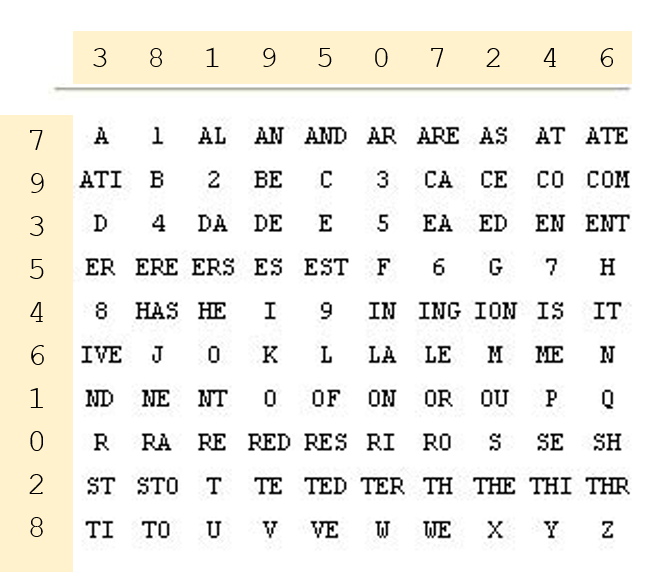
The crypto number table
On the website of crypto collector Nick Gessler, …
… who is a professor emeritus at Duke University, I found a very simple manual cipher that looks quite interesting. It is referred to as crypto number table.
It is obvious how this method works. The table contains 100 entries, each one consisting of a letter, a digit, a letter pair (bigram) or a letter triple (trigram). The bigrams and trigrams represent the most frequent ones in the English language. For encryption, each entry is encoded by its line and column number.
For instance, the cleartext TO BE OR NOT TO BE, when written as TO BE OR N O T TO BE, is encrypted as follows:
TO BE OR N O T TO BE 02 24 77 60 63 93 02 24
It is clear that the table can be easily varied by permuting the numbers indicating the line and the column. Here is an example:
In this case, TO BE OR NOT TO BE encrypts to 88 99 17 66 19 21 88 99.
There are, of course, other ways to change the table, but we only consider line and column number permutations. This means that the key can be provided as two numbers, say 7341589260 and 6048321957. Instead of two numbers, two keywords can be used.
A spy using a crypto number table only needs a sheet of paper with the table written on it (as an alternative, he can memorize the table) and two passwords. This looks like a handy, inconspicuous cipher.
I wonder who created the crypto number table and if it was ever used in practice. Nick’s web page doesn’t provide any information. Perhaps, a reader knows the answer. Otherwise, I will ask Nick when I meet him at a conference next time.
Is the crypto number table a secure cipher? I am sure that it can be broken today with Hill Climbing or some other algorithm. Without computer support, it is certainly a lot more difficult.
A challenge
Here is a text I have encrypted with the crypto number table above (with permuted line and column numbers)
93 83 03 91 84 92 05 91 83 71 08 51 58 80 83 43 88 66 57 97 55
02 54 00 66 12 10 49 35 65 33 50 07 83 33 84 20 88 10 59 65 65 59 70 92 10 59 59 91 54 83 97 02 52 97
97 07 71 12 16 92 10 57 05 91 83 10 90 83 28 52 91 88 69 49 65 59 64 90 91 83 69 37
00 12 16 91 85 70 81 69 81 50 12 92 70 81 60 10 90 21 59 59 64 90 02 74 52
70 49 65 65 01 83 25 16 83 54 60 74 12 07 71 53 40 92 25 36 13 55 77 16 49 25 16 44 82
62 81 65 16 84 40 92 01 80 70 81 65 55 92 16 84 29 16 40 33 92
29 66 25 16 74 52 70 49 65 65 10 40 31 28 59 72 24 51 83 40 47 10 71 03 92 03
40 93 03 71 25 73 50 02
Can you break this challenge?
Follow @KlausSchmeh
Further reading: The low-tech cipher LC4
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/





Kommentare (14)