More about AN0M and Operation Trojan Horse
AN0M, the FBI’s tampered encryption app, made headlines last week. Today I can present some more information about it – including a podcast interview I gave on the subject.
Last week, the FBI, along with several other police agencies alike, set a milestone in the history of crime-fighting and in the history of cryptology: in Operation Trojan Shield, there were over 800 arrests, and enormous quantities of drugs and weapons were seized. It is said to have been one of the largest police actions ever.
AN0M
The investigators achieved this success thanks to a manipulated encryption app called AN0M. The FBI managed to make this software popular among criminals without them having any idea who was behind it. AN0M was designed in such a way that the FBI could read all the messages sent, despite encryption. And that’s exactly what the investigators did: they were able to analyze a total of 27 million messages within 18 months. Numerous suspected criminals delivered themselves to the knife in this way.
Ten days ago, I reported on AN0M on Cipherbrain. Although my article was only one of many in the press on the subject, it was widely read – even though (or perhaps because) I wrote more about the use of encryption by criminals in general than specifically about AN0M. To my delight, someone included my article in the German Wikipedia entry “Trojan Shield” – as the only weblink so far. Thanks to the unknown author.
How did AN0M work?
It is not yet clear to me how the “backdoor” in AN0M worked. It is conceivable that the encryption used was intentionally weak. This could be achieved, for example, by using a random generator to generate predictable or guessable keys. Alternatively, one could use an encryption method that does not encrypt properly.
Another possibility is that the app additionally sends all encrypted data to the FBI unencrypted. However, such a practice can easily attract attention. Does any reader know how exactly the FBI designed AN0M?
My podcast appearance
My article about AN0M also caught the attention of editor David Kopp of the MDR podcast “Spur der Täter”. On Tuesday I gave him an interview. Yesterday, the corresponding podcast episode “AN0M – The FBI’s Crypto Trap” was released. First, it describes Operation Trojan Shield in general. My contributions can be heard from about 16:30 min on, when it is about the technical background.
The story of AN0M
The podcast also tells how AN0M came about. In the beginning, there was an encrypted messenger called “Phantom Secure” that the police were able to infiltrate (similar to EncroChat and Sky ECC) and eventually use as a source of information. The FBI succeeded in recruiting a participant in this case. He was in the process of developing an app called AN0M. To avoid a prison sentence, he offered the FBI to use the app and his customer network. In exchange, the informant with a criminal record received a reward of $120,000 and about $60,000 in expenses.
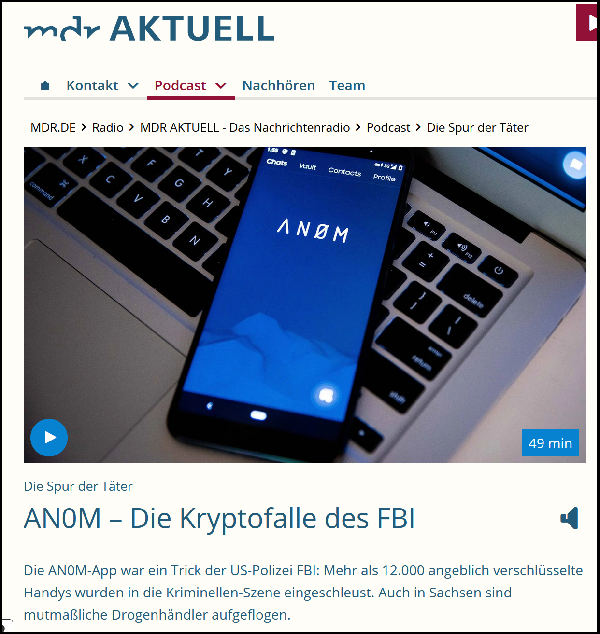
The FBI then set up a company, also called AN0N, which supplied more than 12,000 crypto phones equipped with the app to over 300 criminal gangs in more than 100 countries from Panama. The following figure shows what AN0M’s user interface looked like:
After 18 months, the investigators had had enough and struck a major blow against the app’s criminal users. The consequences are well known. Operation Trojan Shield also had an impact in Germany. According to the Federal Criminal Police Office, 70 suspects were arrested and 150 properties searched in this country.
What’s still to come
The investigation of Operation Trojan Shield will undoubtedly take some time. The editors of the podcast post in question apparently had great difficulty finding interview partners involved in the operation. With the work still in progress, the police are probably avoiding the press.
I hope and assume that nevertheless in the near future still some over the backgrounds of the operation “Trojan Shield” will become well-known. At the latest, when the first arrestees are on trial, the investigators will have to give an insight into their work. Until then, the FBI and others can think about what tricks they can use to catch criminals on the Internet in the future. As blog reader Bomjack correctly noted, the idea of an encryption app honeypot (nothing else AN0M is) should now be burned.
There has been little public criticism of Operation Trojan Shield. But that, too, will surely change. An important question in such wiretapping operations is always how many blameless citizens were also monitored and whether the action was proportionate. The police actions against EncroChat and Sky ECC were not without controversy in this regard. Let’s see who else speaks out.
Not only criminals encrypt
I would also like to mention the comment by blog reader Joachim. He rightly pointed out that not only criminals encrypt, but also dissidents and opposition members in dictatorships depend on effective encryption. This is a topic I would like to blog about. I have already gathered some information on this. If any reader knows anything about this topic, I would be happy to hear from you.
If you want to add a comment, you need to add it to the German version here.
Follow @KlausSchmeh
Further reading: FBI hat iPhone des San-Bernadino-Attentäters geknackt – ohne die Unterstützung von Apple
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/




Letzte Kommentare