Taking the five rows, five columns, and ten diagonals of the left half of the first table, “?” can be encrypted into one of the following 20 groups:
QuG SLH onI Wdv Mlr QoM jaT unl fsi GIr Qnr jsM uIT fol Gai QsT jIl uoi far GnM
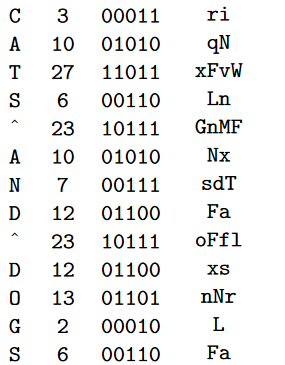
The plaintext CATS AND DOGS can be encrypted as follows (many other substitutions are possible):
rinqNxFvaWLnGnMFNxsdTFaoFLfNlxsnNrLFa
As can be seen, Handycipher can encrypt the same plaintext into a large number of different ciphertexts. Nevertheless, decryption leads back to a unique plaintext.
Adding null characters
So far we have only used the left half of the first table. The right half can be used to make the encryption more secure. Its purpose is to add meaningless letters (so-called nulls) to the ciphertext. A null generated the same way as a ciphertext letter, with the only difference that the right half of the first table is used.
As null can be easily distinguished from ciphertext letters, if one knows the key, the encipherer can include as many nulls as he wants and put them where he wants. However, the specification of Handycipher is much more restrictive. It defines a random-based method that interweaves the ciphertext with a sequence of nulls. For details, please refer to the specification.
How secure and convenient is it
It certainly requires some practicing to use the Handycipher. However, for a trained user it should be possible to encrypt a plaintext with Handycipher in an acceptable speed. But is it secure? I will present a few security considerations, including a number of challenges, in my next blog post.
Follow @KlausSchmeh
Further reading: Bigram substitution: An old and simple encryption algorithm that is hard to break
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/



Kommentare (12)