A recent TV documentary reported on a spy radio transmitter that was placed near an East German army facility. The transmission schedule of this device was computed with a method that is not publicly known. Can a reader reverse-engineer this algorithm?
Blog readers Karsten Hansky and Detlev Vreisleben have provided me some interesting information about a little known spy operation from the last years of the Cold War. The details about this story are covered in a recent German TV documentary. Those who understand German can watch it here.
Operation Hamster
The documentary is about an East German secret service activity titled “Operation Hamster”. This operation started when East German radio stations noticed the existence of an unknown radio transmitter, which transmitted exactly two messages every week. Each message was only 1.3 seconds long.
Extremely short radio messages were nothing uncommon in the intelligence community during the Cold War. Many spies used high-speed data encoding technologies to communicate with their contact persons. A message that was transmitted within a second or even less usually went unnoticed by the enemy. If an adversary radio station did detect the short transmission, it was still difficult to locate the sender.
In order to enable high-speed data transmissions, the secret services developed so-called burst encoders, which could transmit a message encoded in advance within a very short time. I recently blogged about a German burst encoder named KSG from the 1950s, owned and demonstrated by US collector Marc Sachs (a good overview on burst encoders is available on the Crypto Museum website; my book Versteckte Botschaften contains a chapter about burst encoders, too).
Of course, the encoding technology of Operation Hamster was much more advanced than the KSG, which was constructed three decades earlier. Although the Operation Hamster messages were very short, East German radio specialists were able to detect them. As these transmissions were encrypted, it did not make much sense to bother about their content. However, it appeared to be possible to locate the transmitter.
As can be seen in the documentary, it took East German radio experts several months of intensive work, before they finally could locate the sender. It turned out to be dug in the ground close to a road that led to an army facility near Krügersdorf, East Germany, about 20 kilometers from the Polish border. The transmitter was a part of a shoebox-sized device that featured a vibration sensor. Based on the vibrations measured by this device, it was possible to monitor the traffic on the near-by road. Twice a week, the collected data were sent via a burst encoder to a western secret service. The information gained from this source was one of many puzzle pieces this secret service used for analysing East German military activities.
Apparently, a spy working for a western service had placed this sensor device. This spy was never identified, nor is it known which secret service was behind this monitoring operation.
Can you reverse-engineer the scheduling algorithm?
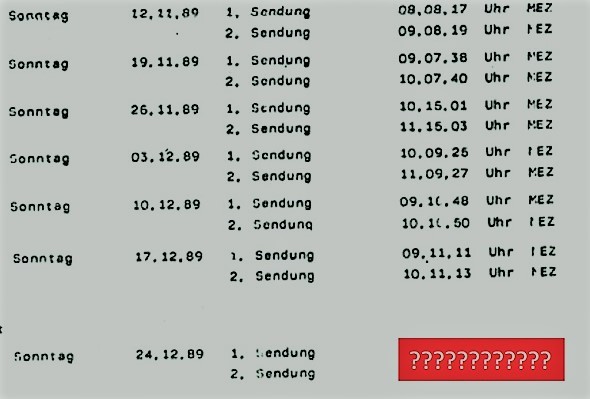
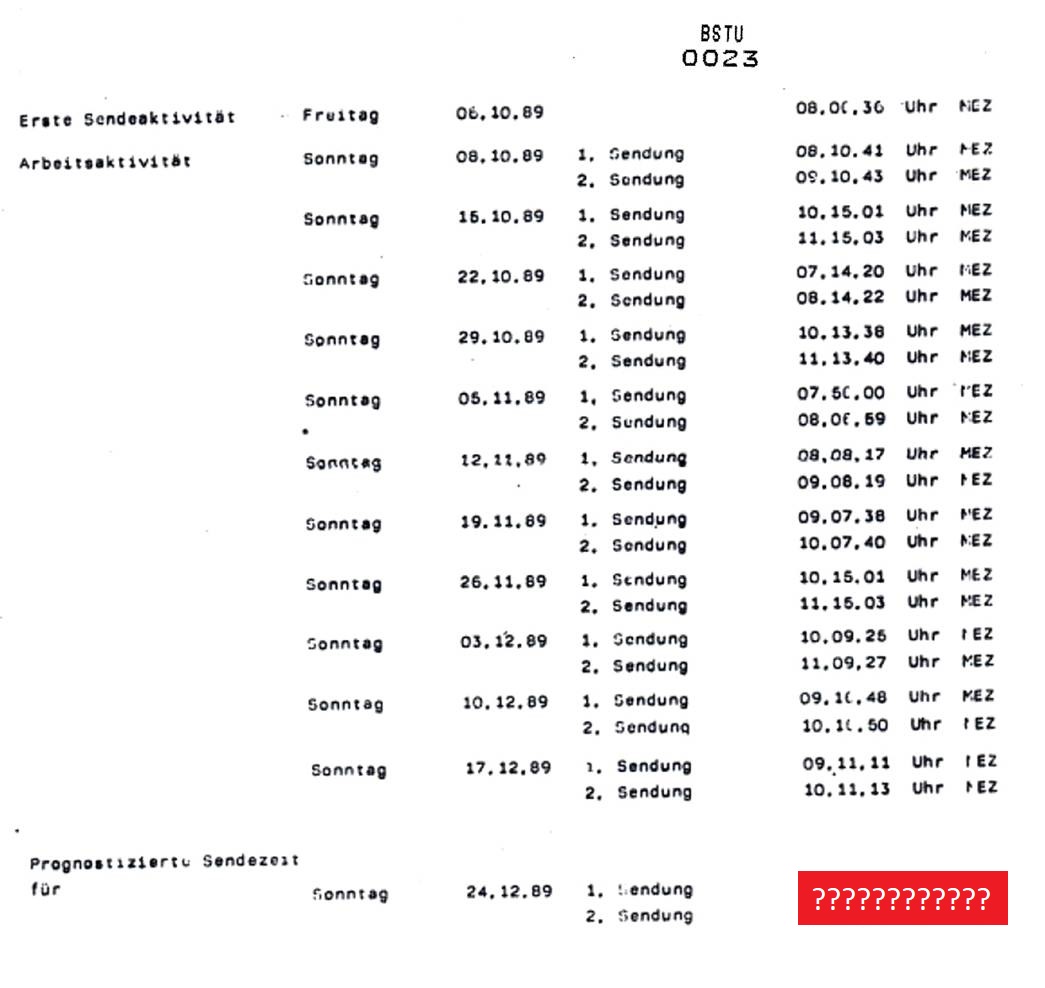
The transmitter of the sonsor device sent only two short messages per week, both on Sunday. The sending time varied. The search for the transmitter became considerably easier when East German specialists found out with which algorithm the transmission schedule was computed. So, they knew the transmission times in advance. However, in the documentary and in the material Karsten Hansky and Detlev Vreisleben provided me, this algorithm is not described.
The following table lists the transmission times on eleven Sundays in 1989:
Based on these 22 transmissions, it was possible to predict the two transmissions on Sunday, December 24, 1989.
According to the TV documentary the algorithm used was reverse-engineered by mathematicians and crypto experts. However, Detlev Vreisleben has found out that it was actually a shift manager of a radio station, who reconstruced the method. This means that the algorithm probably was not too complicated.
Can a reader find out how this algorithm worked? If so, please compute the transmission times of December 24, 1989. These times are known, so it will be easy to verify whether a suggested method is correct.
Follow @KlausSchmeh
Further reading: The ciphers of spy Brian Regan
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/



Kommentare (21)