In a well-known codebreaking book from the 1930s, a Playfair-encrypted message with a (probably fictive) background story is provided. Can a reader break this cipher?
If you’re looking for a good book about breaking classical ciphers, you should try Cryptanalysis by Helen Fouché Gaines. First published in 1939, this work explains numerous ciphers (including MASCs, Vigenère, transpositions and a few others you might know from this blog) and methods to break them.

Of course, Cryptanalysis doesn’t cover computer-based solution methods, such as hill climbing and dictionary attacks, but it’s still the best book about codebreaking I am aware of. In fact, I don’t even know of a codebreaking book that includes computer-based solution methods (note that I am talking about classical codebreaking, not about modern cryptogtaphy), but I am optimistic that one day I will write one myself.
Cryptanalysis provides a comprehensive treatment of the Playfair cipher. Breaking a Playfair cryptogram without computer support is far from easy, as it requires some knowledge about the plaintext (for instance, a word that appears in it) and a lot of trial-and-error work.
How the Playfair works
As explained many times on this blog, the Playfair cipher substitutes letter pairs. So, the cleartext needs to be written as a sequence of letter pairs (the following cleartext is a Shakespeare quote taken from Robert Thouless’ life-after-death experiment):
BA LM OF HU RT MI ND SG RE AT NA TU RE SS EC ON DC OU RS EC HI EF NO UR IS HE RI NL IF ES FE AS T
The Playfair cipher requires that no letter pair consist of two equal letters. Therefore, we add an X between the two Ss:
BA LM OF HU RT MI ND SG RE AT NA TU RE SX SE CO ND CO UR SE CH IE FN OU RI SH ER IN LI FE SF EA ST
If the number of letters in the cleartext is odd, another X needs to be added at the last position, but this is not the case here. Next, we set up a 5×5 matrix containing the letters of the alphabet in a random order (we identify the J with the I, in order to get a 25 letter alphabet):
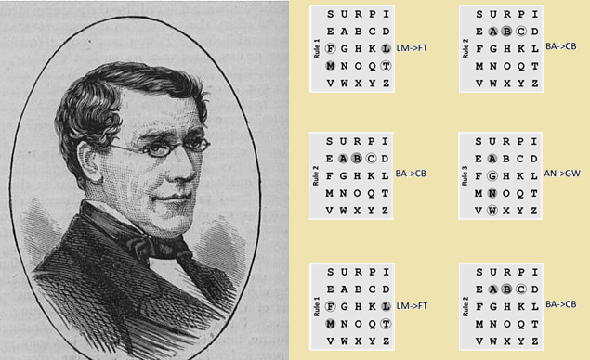
S U R P I E A B C D F G H K L M N O Q T V W X Y Z
As you might have noticed, the letter order in the matrix has been derived with the keyword SURPRISE. It would be more secure to use a completely random order of the letters.
Now, we replace the cleartext letter pairs (BA, LM, OF, HU, …) according to the three Playfair rules. Here are the rules in a diagram:
Here are the same rules in text form (I refer to the letter pair to be replaced as XY):
- If X and Y are not in the same column and not in the same row (this is the most frequent case), form a rectangle and replace the two letters by the other two corner letters (the upper cleartext letter is replaced by the other upper letter in the rectangle, the lower cleartext letter by the lower one). For instance, LM becomes FT.
- If the two letters stand in the same row, each one is replaced by its right neighbor. Here, BA becomes CB.
- If the two letters stand in the same column, each one is replaced by its lower neighbor. In our example, AN becomes GW.
When we apply the Playfair rules on our cleartext with our 5×5 matrix, we get the following ciphertext:
CB FT MH GR IO TS TA UF SB DN WG NI SB RV EF BQ TA BQ RP EF BK SD GM NR PS RF BS UT TD MF EM AB IM
A challange
In Cryptanalysis, Helen Fouché Gaines presents a Playfair cryptogram created by a member of the American Cryptogram Association (ACA) nicknamed Dan Surr. The following background story (probably fictive) is provided:
History: Detective Gettamann, investigating the murder of Francis V. Bacon, well-known traveler, explorer, and connoisseur, has found this message in an envelope addressed to Wm. K. Pierce, former traveling companion of the deceased. Death had occurred during sleep; caused by strangulation with red silk thread. Only clues found: a few grains of sand on the kitchen floor and what appears to be an oriental turban.
Here’s the cryptogram:
YG NG CR FV FZ RI OU KZ CW OW BQ GQ IH HL YW EG
NG QM WX RT KP VE CA IG QI VD QI GN GZ IZ QY QR
HY NG XN AB AK OX NY WC WC TN OX DH NE IH IH YR
IS QY WC HI UI UI IR QE WS RW LG WR AB GW VW CA
RQ XM ER QM RE CW ZI RQ XW QW GH YC AY YO VO NE
RL PG CG WI NX VW CA NX QM LH IG RQ WT GO UI GZ
EG XN IW OU XT WO LH IG RQ XM WS QY TX IR IQ XM
OG DU AB RM AX UM RG ZR XA PM RW LD KG HI XK LC
RT KP VE FO NX XK WR WS QY UR ZX YL AT UI RH TR
AV WS DH WQ PM AK IW OU WT DE IR WX RQ XZ SI GU
QN IR XN IR YN IG GY TR ZX YU RU YL IQ YA RU KG
QM PD QM IT HA WS FE RW GH RB HA QI QM GI QC QR
UL WV AB NX GO HA FR IY QY BN QM YH NG IQ RU YL
IQ BL PK QM RU GU IR TX SI GQ LQ DX XO EV BM CR
FV GV AB GE RZ GQ YH HA RW YM NE YM BL VW PS
I’m sure that the background story provides a number of clues (otherwise, this message would be as good as unsolvable with the methods available in 1939). But these clues are not really obvious. Does the name PEARCE appear in the message? Or the word TURBAN?
With today’s means, especially hill climbing, it should be possible to solve this ciphertext without any knowledge about the content of the message (except that it is written in English). Perhaps, the solution is even already known – after all the challenge stems from a well-known book.
In addition, I would be interested to know who Dan Surr was. Can a reader find this out?
Follow @KlausSchmeh
Further reading: Can you solve these Playfair challenges from 1935
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/



Kommentare (5)