At the hacker conference 44CON 2019, wich took place in September in London, I gave a talk about Cold War cryptography. Here’s a professionally produced video of it.
The 44CON, organized by Steve Lord and Marizel Fourie, is an annual hacker conference held at the IBIS Earl’s Court in London. It’s a great event, though I am usually among the oldest participants with my 49 years of age (at the NSA Symposium for Cryptologic History, which takes place next week, I am still one of the youngest).
44CON
In 2016, I handed in my first presentation proposal for 44CON. It was rejected. One year later, in 2017, I was more successful. In 2018, my submission was accepted again. At 44CON, all presentations are recorded on video and published on YouTube. You can find my two first 44CON talks here:

Schmeh

Schmeh
As it seems, my talks were received very well. So, when earlier this year I handed in a presentation for the 2019 edition of 44CON, it was accepted again. The topics I talk about at this hacker conference are not typical hacker topics, but apparently, the program committee is interested in them anyway.
My Cold War cryptography talk
My third 44CON talk, delivered on September 13, 2019, was about Cold War cryptography (again, not a typical hacker topic). To my surprise, a video of this talk is already available on YouTube. In the years before, the videos were published only a few months after the event. Thanks to Steve and Marizel for making my talk accessible so early this time. Here’s the video:
My talk had four chapters:
- One-time pad encryption: The one time pad played an important role in the early Cold War. Among otger things, I mentioned the Reihenschieber.
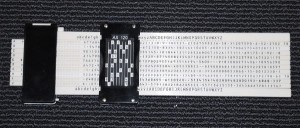
Schmeh/BSI
- Golden Triangle: The Golden Triangle of encryption technology is an area in northern Switzerland. It includes the towns of Zug, Regensdorf and Baden. As good as all commercially sold encryption machines of the early cold war I am aware of were produced in this region. This story is covered in my book Codeknacker gegen Codemacher.

Schmeh
- Feistel in East Germany: This topic is covered in a recent blog post.
- Double columnar: The double columnar transposition is an encryption method used in the Cold War.
Any questions, critics and suggestions about my presentation are welcome. I plan to hand in another talk for 44CON next year. Again, it will not be about a typical hacker topic, but about something historical. There’s always a lot of competition among the submitters, as the 44CON is a popular event. I hope my submission will be successful.
Follow @KlausSchmeh
Further reading: More about the Arno Schmidt cryptograms
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/



Kommentare (3)