Analysis by Tobias Schrödel on the insecurity of passwords
Blog reader Tobias Schrödel has created a letter frequency analysis for passwords. Unlike in German or English texts, the letters X, Y and Z are not uncommon in passwords.
It was already known in the 1980s that passwords lead to security gaps. The group around Karl Koch and Markus Hess, which became known as the KGB hackers and was smashed in 1989, penetrated many systems with a simple trick: they tried to see if the default password set by the manufacturer still worked. Often enough, this was the case.
Password weaknesses
Even if a password is written down, this can be an invitation for hackers. The US American Stanley Rifkin was responsible for the classic in this area in 1978, when he used a password that he had read to steer 10.2 million US dollars into his account.
Another trick is phishing. In this case, the user is made to believe that he has to visit a certain website (for example, that of his bank) and enter his password there. However, the website is not real and only has the purpose of stealing the password.
But there is an even simpler way. Some people will reveal their password if you ask them nicely. US comedian Jimmy Kimmel has tried it out:
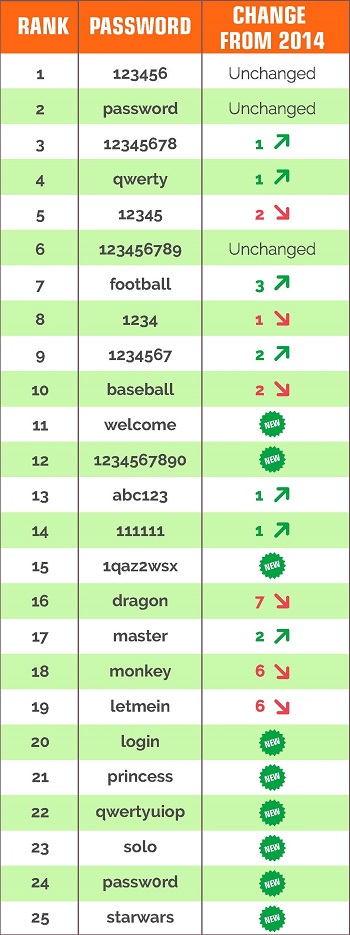
As I have reported several times on Cipherbrain, a hacker can also try it with particularly popular passwords. For years, “123456” has been at the top of various analyses. Also “12345”, “qwertz”, “hello” or “password” are popular. In addition, you can try using a user’s first or last name, in some cases spelled backwards.
Brute Force
Fortunately, many people use passwords that are not in a dictionary and that do not result directly from the arrangement of letters on the keyboard. However, a hacker is not completely powerless against such constructions. The common password guessing programs support a so-called brute force function for this purpose. This means: They try out all possible passwords of a certain length.
However, the brute force method is not very effective. If you assume 70 characters (uppercase letters, lowercase letters, digits and a few special characters), there are already almost 2 billion possibilities for five-digit passwords. A computer can still manage this, but with eight digits you already end up with 500 quadrillion, which is hardly realistic.
However, these numbers are theoretical. In practice, for example, most people use more letters than numbers and special characters – “kshd24!” is therefore more likely than “§!&3§f”. This already limits the search space significantly.
Tobias Schrödel’s analysis
Tobias Schrödel, known to readers of this blog as a comedy hacker and collector of encrypted postcards, recently published a study on character frequency in passwords. As it is known in cryptography, he has created corresponding frequency analyses. The results can be found on his web page. Heise has also reported on this.
Tobias has evaluated over 2.5 billion passwords. His source was bigDB. This contains several billion email addresses and associated passwords that have come to light in various security incidents over the years.
Tobias broke down his results by country (top-level domain) and in some cases compared them to the letter distribution in texts of the language spoken there. The results can be used to significantly speed up brute force attacks on passwords. Here are a few findings from Tobias’ analysis:
The most common letter in English and German is E, but in passwords it’s A.
The letters X and Y occur up to 50 times more frequently in passwords than in texts.
Asians use two to three times more digits in passwords than the rest of the world.
The T is used much less frequently in passwords than would be expected (up to 50 percent less).
It is unclear in many cases how these phenomena come about. Does any reader perhaps know why Asians use so many digits?
Passwords are no longer up to date
Tobias’ analysis shows once again: passwords are no longer up-to-date on the Internet and should be replaced by more secure methods. There are many possibilities. For example, in addition to the password, one can use a one-time password that is sent to the user via SMS. Even better is to use a smart card or a token.
The only problem is that all these measures require additional effort. However, with the numerous security gaps that passwords cause, there is no getting around the alternatives.
If you want to add a comment, you need to add it to the German version here.
Follow @KlausSchmeh
Further reading: Serienmörder stirbt und nimmt Verschlüsselungspasswort ins Grab
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/





Letzte Kommentare