
Alles wichtige zum Thema Post-Quanten-Kryptogafie auf 25 Seiten – das gibt es in meinem kostenlos erhältlichen Whitepaper “Post-Quanten-Kryptografie – verständlich erklärt”.
Der niederländische Taschen-Fernschreiber TX-1000 verschlüsselte zunächst mit dem DES-Verfahren. Doch dann setzte die NSA ein anderes Verfahren durch. Eine neue Forschungsarbeit zeigt, dass sich dieses einfach knacken ließ.
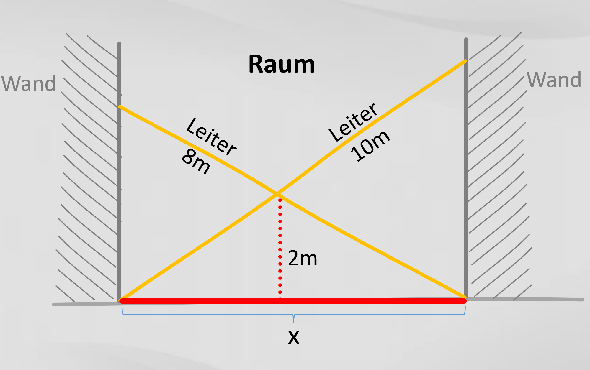
Im Zusammenhang mit der Post-Quanten-Kryptografie spielt das Problem der gekreuzten Leitern eine Rolle. Es ist einfach zu erklären, aber nur schwer zu lösen.
John Haas and Christian Baumann, two blog readers who met when I invited both of them to a get-together in Vienna, have started an interesting project.
A French expert team has succeeded in factorizing a 795 bit prime number product. This is a new world record. The old one (768 bit) dated from 2009.
IT security experts have cracked a number of passwords used by Unix pioneers in the late 1970s.
At the NSA Symposium on Cryptologic History, I will give a presentation about brute-force attacks. There’s one thing I still haven’t figured out: when was the first brute-force described or carried out?
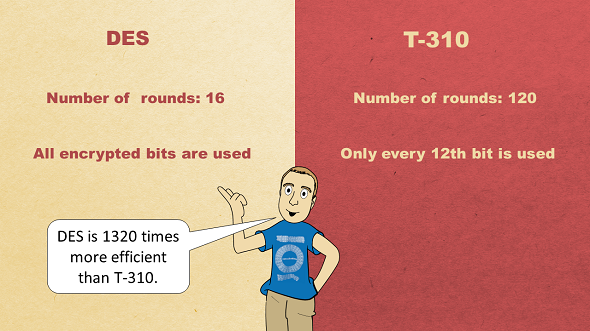
In the early 1970s, cryptographers in the USA and in East Germany developed two suprisingly similar encryption methods. Did one party steal from the other? Or was a useful concept invented twice?
In 1999 cryptographer Ron Rivest published an encrypted text that was designed to take 35 years to break. Apparently, it has now been solved.
US standardization authority NIST has published the algorithms that participate in the Post-Quantum Crypto Competition. No fewer than 69 crypto systems enter the race.









Letzte Kommentare