The longest key ever publicly broken by exhaustive key search was 64 bits long. If you solve the cryptogram I introduce in this blog post, you can set a new record.
Everybody interested in codebreaking should know the web site Mystery Twister C3 (MTC3). MTC3 is a site dedicated to crypto challenges, ranging from pretty easy to hitherto unsolved. If you solve one of these challenges, you get a certain amount of points. The most successful players are listed in a hall of fame.
MTC3 is organized by Prof. Bernhard Esslinger (University of Siegen), Prof. Dr. Alexander May (Ruhr-University Bochum) and Prof. Dr. Arno Wacker (University of Kassel). There’s a close relationship to the open source crypto training software CrypTool.
The challenges
The challenges of MTC3 are devided into four levels: level 1 (easy), level 2 (intermediate), level 3 (hard) and level X (unsolved). The following postcard is presented as a level 1 challenge:
I have been involved in MTC3 myself, too, as a provider of a number of challenges. All of them are either level 3 or level X, which means that I delivered some of the tough ones. Some of my challenges represent well-known crypto mysteries, like Kryptos, Dorabella, Beale Ciphers or D’Agapeyeff. In addition, I provided the DCT challenge, which was solved by George Lasry, and two M-138 challenges.
The World Record Challenge
Another one of my MTC3 challenges is titled “World Record Challenge”. It refers to the fact that the longest key ever publicly broken by exhaustive key search was 64 bits long. This world record was set by a team of experts in 2002 after five years of computation. More information is available at Wikipedia (see „RSA Secret-Key-Challenge“) .
The purpose of the World Record Challenge is to improve the current world record by one bit. This means that a 65-bit key is to be cracked by exhaustive search.
The ciphertext I took was encrypted with CrypTool. The encryption algorithm used is AES in ECB mode with a key length of 128 bits. The first 65 bits must be guessed. The remaining 63 bits are set to 1.
The first eight bytes of cleartext represent the solution to be handed in at MTC3. They form an English word written in capital ASCII letters. The remaining eight bytes have the value „CrypTool“ (in ASCII code) or 43 72 79 70 54 6F 6F 6C (in hex code).
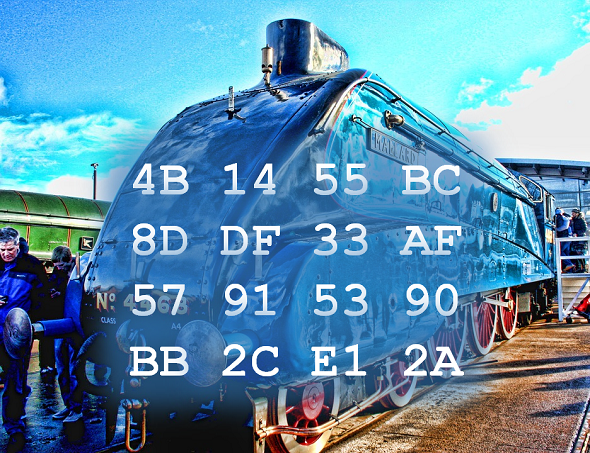
Here is the ciphertext of the World Record Challenge (in hex code):
4B 14 55 BC 8D DF 33 AF 57 91 53 90 BB 2C E1 2A
This challenge is certainly a tough one – after all, solving it means a new world record. However, as computer technology has considerably improved since 2002, it should be possible to find the solution in much less than five years. If we assume that computation power doubles every 18 months (Moore’s law), the time needed will be a thousand times less. Instead of five years (~ 1800 days) this would mean 1.8 days, provided that the same hardware budget is available.
I think, after 14 years it is time to improve this record. I wish you good luck trying it!
Follow @KlausSchmeh
Further reading: UK crypto blogger Nick Pelling has just posted a campaign on Kickstarter to make a documentary about a 200-year-old pirate treasure mystery involving encryption: https://www.kickstarter.com/projects/nickpelling/gold-beyond-your-dreams




Kommentare (5)