Designing a secure and convenient encryption algorithm that doesn’t require a computer program or a machine is quite a challenge. The Handycipher is an interesting method of this kind.
Imagine a spy operating in a foreign country, who needs a method for encrypting messages to his contact person. Using an encryption machine, like the Enigma, or some other cipher device is prohibive in this situation, as this might raise suspicion. Nowadays, a computer program would do this job, but computers were not available until a few decades ago.
For the reason mentioned, the design of purely manual ciphers has played an important role in cryptography for centuries. However, this has proven a hard problem. It is extremely difficult to design a purely manual cipher that is both secure and convenient – especially if it is desired that such a cipher withstands modern cryptanalysis.
Today, the Double Column Transposition (DCT, also known as double cube), is considered one of the best manual ciphers. George Lasry has pointed out that ADFGVX (a World War I cipher) is another interesting candidate, provided that the second step of this method (a transposition) is carried out twice.
Others have suggested encryption algorithms that use unsuspicious aids, such as Rubik’s cube encryption and Solitaire (uses a deck of cards). Recently I heard of a new manual cipher named Elsiefour – I will certainly take a closer look at it soon.
The Handycipher
Today I am going to introduce another manual encryption system: Handycipher. It was created by Bruce Kallick a few years ago.
Handycipher encrypts each plaintext letter into a letter group. This means that the ciphertext is longer than the plaintext. Such a property is usually not desired. Among other things, it results in the fact that an encrypted file needs much more storage space than the plaintext file.
However, when it comes to manual ciphers (especially, spy ciphers), writing five letters instead of one is acceptable, especially, if this avoids a lengthy and cumbersome encryption procedure.
Handycipher encrypts text strings taken from a 31-character alphabet comprising the 26 uppercase letters together with the five
symbols “,”, “.”, “-“, “?”, and “ˆ”. Here’s an example of a plaintext:
CATS AND DOGS
Handycipher ciphertexts are strings over a 50-character alphabet comprising of the letters A, B, …, Y and a, b, c, …, y.
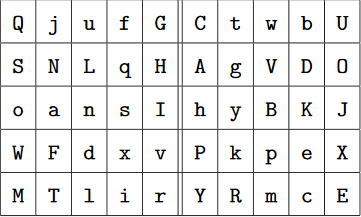
A Handycipher key is a permutation of the 50 letters of the ciphertext alphabet and the symbol “ˆ”. Here’s an example key:
QjufGCtwbUSNLqHAgVDOoansIhyBKJWFdxvPk^peXMTlirYRmcE
The key (without the “ˆ” character) is written in a table with ten columns and five rows. Using our example key this looks as follows:
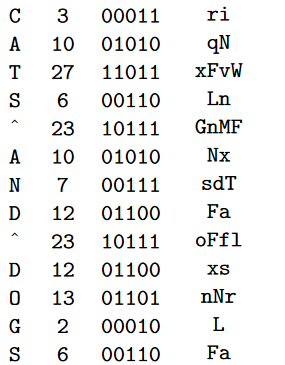
A second table is derived by omitting the 20 lowercase letters f-y and substituting the characters “Z”, “,”, “.”, and “?” for the letters a, b, c, d, and e. As Q is the first letter in the table above that is not omitted, it is assigned to the number 1. G, the second letter not omitted, is assigned to 2. C is assigned to 3, and so on. Here’s the second table:
The numbers in the lower line range from 1 to 31. For the encryption process we need the binary representation of each number: 1=00001, 2=00010, 3=00011, …, 31=11111.
As an example, let’s now encrypt the plaintext character “?”, which is represented by 21 = 10101. As one possibility, “?” can be encrypted to QuG, because the first line of the left half of the first table is QjufG and 10101 indicates that the first, the third and the fifth letter have to be taken. Alternatively, “?” can be encrypted to SLH, because the second line of the same table is SNLqH.
Taking the five rows, five columns, and ten diagonals of the left half of the first table, “?” can be encrypted into one of the following 20 groups:
QuG SLH onI Wdv Mlr QoM jaT unl fsi GIr Qnr jsM uIT fol Gai QsT jIl uoi far GnM
The plaintext CATS AND DOGS can be encrypted as follows (many other substitutions are possible):
rinqNxFvaWLnGnMFNxsdTFaoFLfNlxsnNrLFa
As can be seen, Handycipher can encrypt the same plaintext into a large number of different ciphertexts. Nevertheless, decryption leads back to a unique plaintext.
Adding null characters
So far we have only used the left half of the first table. The right half can be used to make the encryption more secure. Its purpose is to add meaningless letters (so-called nulls) to the ciphertext. A null generated the same way as a ciphertext letter, with the only difference that the right half of the first table is used.
As null can be easily distinguished from ciphertext letters, if one knows the key, the encipherer can include as many nulls as he wants and put them where he wants. However, the specification of Handycipher is much more restrictive. It defines a random-based method that interweaves the ciphertext with a sequence of nulls. For details, please refer to the specification.
How secure and convenient is it
It certainly requires some practicing to use the Handycipher. However, for a trained user it should be possible to encrypt a plaintext with Handycipher in an acceptable speed. But is it secure? I will present a few security considerations, including a number of challenges, in my next blog post.
Follow @KlausSchmeh
Further reading: Bigram substitution: An old and simple encryption algorithm that is hard to break
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/





Kommentare (12)