Five years ago I asked my readers for information about seven little-known cryptograms created by criminals. Meanwhile, I’m a little wiser, but I still would like to know more about some of these encrypted messages.
Crimes that involve encryption have always been a popular topic on this blog and in my books. My posts about the Zodiac Killer, the Somerton Man, Ricky McCormick’s encrypted notes and similar stories repeatedly received many page hits.
While the cryptograms of the Zodiac, the Somerton Man, and McCormick are well documented, there are other criminal cases involving cryptography about which I have much less information. When in 2015 I set up a list of crimes that included encryption I knew nothing about, I came up with six cases. Like always, when I have an open question about a crypto history topic, I asked my readers for help. My blog post (in German) about these six cases was published in 2015. In an addendum I added a seventh one.
Meanwhile five years have passed and, much to my delight, I have been able to solve some of these mysteries. So, here’s my update.
1. Nina von Gallwitz kidnappers
The then eight-year-old Nina von Gallwitz from Cologne, Germany, was kidnapped in 1981 and released after 149 days against payment of a ransom. The perpetrators were never caught. Two negotiators hired by the Gallwitz family communicated with the kidnappers via encrypted newspaper advertisements. According to Wikipedia, the “five-line Caesar” cipher was used (this is a term I was not familiar with). Neither the Wikipedia article no any other source I consulted mentioned any details about the crypto involved.

Source: Die Welt
A few weeks after publication, I received a mail from blog reader Rolf Thelen. He knew the details of the case and provided me all the information I was looking for, including scans of the newspaper ads. I was overwhelmed and hereby want to thank Mr. Thelen again. Here’s the blog post I subsequently wrote (in German).
2. Victor Lustig (imposter)
Victor Lustig (1890-1947) was a famous trickster and imposter. His most famous coup was the “sale” of the Eiffel Tower to a French scrap metal dealer from whom he took a handsome sum. According to the book The Man who Broke Purple (p. 124) by Ronald Clark, codebreaker William Friedman deciphered an encrypted message created by Lustig in 1936. Details about this story were not known to me.
In 2018, I visited the Marshall Library in Lexington, Viriginia, to do research in the William Friedman collection. There I found the message Clark probably referred to in his book. As it turned out, Lustig’s writing was not encrypted but written in misspelled German. Nevertheless, the mystery was now solved. Check here for my blog post about this story.
3. Petras Dominas (murderer)
Petras Dominas was a murderer with the reputation of being highly intelligent. According to an article in Der Spiegel, he used a complex encryption system of his own design. The only thing I knew about this cipher was the following small excerpt from one of Dominas’ writings:
Dominas’ encryption system is still a mystery to me. If a reader knows more about it or can make sense of the snipet above, I would be very interested to learn.
4. John Wilkes Booth (Abraham Lincoln murderer)
In 1865, actor John Wilkes Booth murdered US president Abraham Lincoln. Booth had several accomplices with whom he communicated via encrypted messages (check here for more information). Unfortunately, I had no information about the cipher Booth used when I wrote my 2015 post.
Still today I don’t know how Booth’s encryption system worked, but I at least I have found out something else: In the 2007 movie National Treasure: Book of Secrets, John Wilkes Booth’s diary plays a role. It is encrypted in a Playfair cipher. However, the plot of this film is ficticious and to my knowledge the real John Wilkes Booth didn’t leave behind an encrypted journal.
5. Ohio prison
Another story covered in the book The Man who Broke Purple (p. 124) by Ronald Clark is about an encrypted message that was seized in the state prison of Ohio. Master codebreaker William Friedman broke this encryption and thus uncovered an escape plan. However, Clark’s book doesn’t explain how the encryption worked.

Marshall Library
During my visit in the Marshall Library in 2018 I was able to find the prison message Clark refered to. Here’s my blog post about it.
6. Adolf Eichmann (Nazi war criminal)
Adolf Eichmann (1906-1962) was one of the most important desk criminals in the Third Reich. Heading a division in the Reichssicherheitshauptamt (RSHA) he organized the deportation and murder of about six million Jews. In spite of his powerful position, he was almost unknown to the public. He admired Adolf Hitler, but never met him in person.
After the war, Eichmann escaped to Argentina, where he began a new life. But his past caught up with him: in 1960 he was kidnapped by the Israeli secret service Mossad and brought to Israel. In a sensational trial he was sentenced to death and subsequently executed.
Much has been written about Adolf Eichmann, but only very few authors mention that in 1950 he sent an encrypted message to his wife Vera. It goes without saying that I would be interested in reading this message and learning about the encryption method Eichmann used, but neither before nor after my 2015 post I couldn’t find out anything about these things.
7. Al Capone
In an addendum to my 2015 blog post I mentioned the infamous gangster boss Al Capone. Capone’s eventual conviction on tax evasion charges was largely supported by evidence from encrypted ledgers. Federal agents successfully proved to a jury that enciphered entries in the ledgers represented payments for alcohol. Check here for details. To my regret, this source doesn’t mention anything about the cipher Capone used. My readers couldn’t provide information about this topic either.
Should a reader have more information about any of these cases, I would be interested to know.
Follow @KlausSchmeh
Further reading: Four cryptograms from a 1926 crime story series
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/



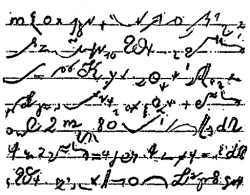



Kommentare (8)