Forgery in cryptology (1)
There are a surprising number of encrypted documents that are, or at least could be, forgeries. Today I present five of them.
First of all, some information that has nothing to do with today’s topic:
The ICCH forum, where I have given several webinar talks, now has a very nice web page. Cipherbrain reader Patrick Hayes created it. On this web page you can read that US professor Chris Christensen will give a talk today at 6 pm (German time) about Japanese encryption machines before and during World War II – an exciting topic, if you think for example about the legendary “Purple”, which was cracked by William Friedman. The dial-in link was sent via the mailing list. If you don’t subscribe to the list and still want to be on it (it’s free) feel free to send me an email.
By the way, the aforementioned Chris Christensen published a very positive review of my recent book “Codebreaking: A Practical Guide” in Cryptologia a few days ago – unfortunately, access to this article is more than twice as expensive as the book itself.
My next ICCH talk will be on March 20, 2021. It will be on the Zschweigert Cryptograph.
Forgeries in cryptology
Now let’s get to the real topic: forgeries. Many things are forged: money, paintings, antiques, written documents. Even fake wines and fake fossils have made headlines.
However, as far as I know, no one has ever systematically dealt with forged encrypted messages. Yet there are more than enough of them. So it’s high time to start a survey. In the following I present a few ciphertexts which are or could be forgeries with a certain probability. There will be more in a few days in another article on the subject. I will of course gladly accept suggestions from readers.
When it comes to forgeries, a statement by art historian Joe Nickell, who is considered one of the leading experts in the field (and who, like me, is a member of a skeptic organization), always comes to mind. Nickell said, mutatis mutandis, “To find out if you are dealing with a forgery, there are three main criteria: provenance, provenance, and provenance.
Provenance refers to the origin of an object, with its previous owners being of particular interest. Nickell means: If it is not quite clear where an object comes from and who owned it before, one should be suspicious of a forgery. In my following considerations, I will therefore always refer to the provenance.
The Beale Cryptograms
Probably the best known forgery in the history of cryptology are the Beale cryptograms. These are three encrypted texts allegedly written by a certain Thomas Beale in the early 19th century in the USA. The following picture shows one of them:
The Beale cryptograms supposedly describe the location of a treasure that Thomas Beale hid in Virginia. Only one of the three Beale cryptograms has been solved, but the information it contains is insufficient to locate the site in question. For over 130 years, treasure hunters and amateur cryptologists have tried in vain to solve the two remaining cryptograms and find the treasure.
Spoiler: No one will ever find the treasure in the future. It simply does not exist.
The reason for my assessment: The whole story about the Beale treasure and the Beale cryptograms is full of inconsistencies. It starts with the fact that the only source for it is a book published in 1885 by one James Ward (“Ward booklet”). Not a single point of the Beale story is confirmed by any other source.
As you can imagine, Thomas Beale could never be linked to an actual person. The gold mine in New Mexico, from which the treasure is supposed to come, was never found. The encryption method used for the second (solved) message does not fit into the time and does not work as described.
It would go beyond the scope of this article to list the numerous other contradictions surrounding the Beale treasure. In the end, it is clear that the story was invented. Thus, the three Beale cryptograms are also fakes.
And what about the provenance of the Beale cryptograms? As expected bad: The originals of the three messages were allegedly lost in a fire. Apart from the author of the Ward booklet, no one has ever seen them.
SS radio message
Nick Gessler, a U.S. professor, has an interesting collection consisting of cipher machines, cipher forms, cipher disks, encrypted postcards and more. There are many unique pieces among them. Among them is the following piece of paper that Nick showed me a few years ago:
This form was allegedly filled out by a member of the SS in 1944. Presumably it is supposed to represent a coded radio message. Interesting and very unusual are among other things the various special characters in the middle column. Up to now nobody could decipher the message.
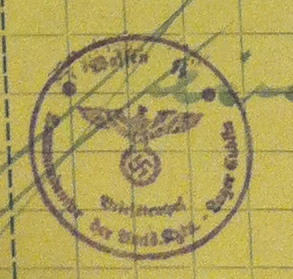
When I presented this cryptogram again on my blog in early February, several readers were sure that it was a forgery. For example, the following stamp is doubtful:
Cipherbrain reader Gerd wrote: “The fantasy stamp used can be found again and again on documents offered as ‘souvenirs’ for collectors on the Internet, e.g. here (SS: Fantasie-Prämienschein über 1 RM).” Thomas Bosbach, TWO, Kerberos, Max Bärtl and The_Piper mentioned further arguments against the authenticity of the document.
And the provenance? Nick Gessler probably bought this piece of paper from a dealer or a private person. I don’t know anything more specific than that.
Flash ciphers
In 2011, an unnamed person contacted Nick Pelling, a leading expert on historical cryptograms. This person told of an encrypted book found shortly after World War II in a wooden box that had been accidentally uncovered in London by a German bomb. In reference to the Blitz, Pelling referred to the manuscript as the “Blitz Ciphers.” On my Encrypted Book List, the Blitz ciphers are number 00014.
The owner of the flash ciphers initially provided Pelling with only three page scans. Pelling presented these on his blog. Later, the owner gave Pelling five more page scans. This makes a total of eight pages on Nick Pelling’s page on lightning ciphers. A transcription is also given there. So far, no one has been able to solve the encryption.
I have blogged about the Blitz ciphers several times before. My readers have largely agreed that it is a fake. Charlotte Auer wrote, for example:
To me these pages look like a relatively simple fake. The paper seems to be artificially aged (mostly with tea or coffee) mold paper that was never bound into a book. In case of an old book at least one side of each sheet (left or right) would have been cut and you would see the little holes of the stitching and other clear marks of former binding.
Almost all “glyphs” are very well known symbols of medieval alchemy, medicine, astrology and hermeticism and can easily be decyphered. Such a decoding would show whether the text is meaningful or not, and what language is underlying it. At a first glance I don’t see any typical structure of a medieval kind of text. I guess it’s either complete senseless or phantastic nonsense in modern English.
Perhaps a little joke just to test Nick Pelling’s cypher skills? At least the “making of” that funny fake was very time consuming and so would be the decypherment. I’m not shure if I should give it a try because the symbols are easy to identify, but obvoius fakes are boring me.
The information on the provenance of the lightning ciphers is also more than scanty. The current owner of the book is not known. Whether the book was actually found during the Second World War cannot be verified today. How and why the book got into the said wooden box and to the later place of discovery is completely unclear. All in all, there is not even any evidence that the Blitz ciphers existed at all before 2011.
The Anthon Transcript
For the Mormons, the Book of Mormon is a sacred scripture and equal to the Bible. According to legend, this work came into being when in 1823 an angel appeared to Joseph Smith, who later founded the religion, and gave him a golden book. This was written in an ancient language (Reformed Egyptian) and in an unusual script (Reformed Egyptian hieroglyphics). The angel told Smith to translate the book into English, which Smith did. The result was the Book of Mormon.
Unfortunately, the golden original of the Book of Mormon is lost. At least a few alleged lines from it have survived in the original script. Smith himself is said to have copied these lines. This transcript is known as the “Anthon Transcript” – named after a scholar named Charles Anthon, who examined the note in 1828. Anthon is said to have initially expressed a positive opinion of the transcript. Later, he changed his mind. Unfortunately, it is not clear whether the document traded today as the Anthon transcript is identical to the one examined by Anthon.
The Anthon transcription (or what is thought to be one) is not legible – apart from the heading “Caractors”. What is particularly perplexing: the letters of the transcript do not look like ancient hieroglyphics with the best will in the world.
The cryptogram expert Nick Pelling even noticed that many of the letters look as if they were taken from one of the numerous shorthand scripts of the 19th century. Nevertheless, it is probably not a shorthand text, because many letters are too complicated for a quick writing (or do other laws apply to angels when writing?). That the letters of the Anthon copy originate from the antiquity is as good as impossible.
Unfortunately, I do not know much about the provenance of the Anthon transcription. As far as I know, the document cannot be traced back to the founder of religion Joseph Smith. That the contents are from an angel probably can’t be proven unequivocally either.
Zodiac copycats
The encrypted confession letters of the Zodiac killer are among the most famous encrypted messages ever. So it’s all the nicer that Cipherbrain readers Dave Oranchak and Jarl Van Eycke, along with Samuel Blake (I don’t know if the latter also reads my blog), solved the second cryptogram in this series last year.
At least in terms of sending anonymous encrypted letters, the Zodiac Killer had several imitators. Some of them even pretended to be the Zodiac Killer – so their letters are fakes. For example, the following letter allegedly written by the killer himself is from 1971:
Here is the letter in somewhat larger resolution. I have no further information about it. That the letter is from the real Zodiac killer is extremely unlikely. Maybe a reader knows more about this forgery or can even solve the encryption.
The issue of provinciality is quickly settled here. Of course, there is no evidence that the real Zodiac Killer ever held this note in his hands.
Conclusion
There are no doubt different reasons to forge a coded text. Sometimes it is greed for money (this might have been the motive with the SS-radio cipher and possibly also with the Blitz ciphers), sometimes it is the desire to prove a dubious story (as with the Beale cryptograms and with the Anthon transcript), sometimes it is pomposity (with the Zodiac imitators).
In the second part of the article series I will present more examples. Maybe – with the support of my readers – it will even be enough for a third article.
If you want to add a comment, you need to add it to the German version here.
Follow @KlausSchmeh
Further reading:
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/










Letzte Kommentare