Still unsolved: Five encrypted radio transmissions of a New York Nazi spy
The coded messages of a World War II spy have puzzled for decades. Can my readers shed light on the mystery?
One of the pleasant side effects of my current book “Codebreaking: A Practical Guide”, which I published in English together with Elonka Dunin, is that I am currently being invited to give talks or interviews in the English-speaking world more often. In mid-July, for example, Elonka and I will be guests on a US podcast to talk about spy encryption techniques.
There are plenty of topics to talk about, after all, I have often reported on spies and their ciphers on Cipherbrain. Think of Brian Regan (“The spy who couldn’t spell”), chancellor spy Günter Guillame or John Anthony Walker. Or of the doll spy Velvalee Dickinson, about whom a chapter is included in my book “Hidden Messages”. When said podcast episode is released, I will of course blog about it.
If the opportunity arises, Elonka and I will also address the Koehler cryptograms in that interview. These are five encrypted radio messages sent to Germany by a spy from New York during World War II. I have blogged about the Köhler cryptograms several times, but so far no one has managed to crack these messages. On the occasion of the mentioned podcast appearance I would like to try again today. Maybe my readers can contribute new clues.
The background
The standard work on German espionage activities in the Third Reich is the book “Hitler’s Spies” David Kahn. The latter is also known to have written the legendary crypto history book “The Codebreakers”, but that one should not be of interest here.
As Kahn reports in “Hitler’s Spies,” the Abwehr (this was the main German intelligence service at the time) managed to recruit a spy in New York who went by the name “Koehler.” What this spy’s real name was and who he was is not known. Presumably, Köhler had no access to secret information and therefore drew his information from everyday observations. According to Kahn, he reported, for example, on U.S. officers he met at a hotel bar who blurted out more or less interesting things. Kahn suspects that Köhler was partly under the influence of the FBI, which is why his reports to the Abwehr may have been doctored.
Nothing more is known about Köhler. Cipherbrain reader Max Baertl brought to my attention that there was a German spy in World War II named Walter Koehler who lived in New York. That would fit, but Koehler was ordered back to Germany in 1941 – three years before the cryptograms were created.
What’s not in “Hitler’s Spies”: In the course of his research, David Kahn came across five coded messages originating from or concerning Koehler, which the Abwehr forwarded internally to Paris in February 1944. At the time, information about the expected Allied invasion was being gathered in Paris. In 1981, Kahn published these five cryptograms in the journal Cryptologia (April/1981 issue).
To my knowledge, this exciting crypto-mystery was not subsequently appreciated in the literature.
The cryptograms
Here is the letter Kahn found with the five encrypted messages (the numbers obviously stand for the length of each message):
An
Abwehrleitstelle Frankreich
Paris Funkstelle
Sofort vorlegen!
Betr.: Koehler
237
Ybtat mqfvo dvbis prito kecqg kokik kyiwm zuarj
alyia qtxvi vxzya szgou skiqn rbqjq nogex ezdnf
vusda zurop ixklo cmnbl grdhz swmch kupef pzlej
hbord wkkhu vthjk sfwda jepmu izvig kzlau rdrxx
mdecs spozv eeeod dlmdz nqmia pidwg xdcyy mvkso
hmmii impwq nkipa mljvm sqsbb glevn sktlq tn.
178
Eekao parwo xiavy pejux lhnjh pbqdd vdvxb mdiia
gwymn zbivm abuws dwoug djozl ylaug loaea ilihj
swjft oetad tjisn avaqn sodwb wzaxe zvoxg xpgzv
adurm shvxx xfmuq pdpvq dqwtu fryok xfvcp ydzwm
ofwfl uzfne qsslo avl.
137
tziqb lqqxs kinod mbvil sukms syarh mhzvp tvswm
ayddg rixyy omfzm ugfzz aznqe ljuyi ygwuo qmdbi
vcxgz rmzno pessh gpoyx qqlei xmaoj buugz czfdl
yzmkp gsmfm dteze oxmos.
140
dmxkb kqnvh zzeek beoop ygcca yvepv tykmt iykfl zkacv
uxiyd kruwy vnjvp xyeqp jpmfo abzpt mjtdy zvzky bjgze
vdtyd zeejw zumjp ivsna gsmzq dltxb qjqqj fnpta mqted
skijj.
229
fpoxa tijyp qrerq znqst zasnk zarvq hhsmw vlhfg pyhqc
yuirf fsgoi twgdg sbphc fkfza bpegh jzujn wtsxp ijamg
tzdto hxzdn uivww tizoc axkye lhmdn sfzjo omrhb zpith
hkisf anvdr ynhqk syrgi ltxos wabom dzwlb byava sjomn
qqszs adddu greao albon lxzgi iwpnf uzgui jgmya ksqfw
zsjl.
Solution approaches
My readers have provided over 50 clues to the Köhler cryptograms over the years, but no one has been able to solve these radio messages. It is not even clear whether Köhler encrypted these messages himself or whether another Abwehr employee did so.
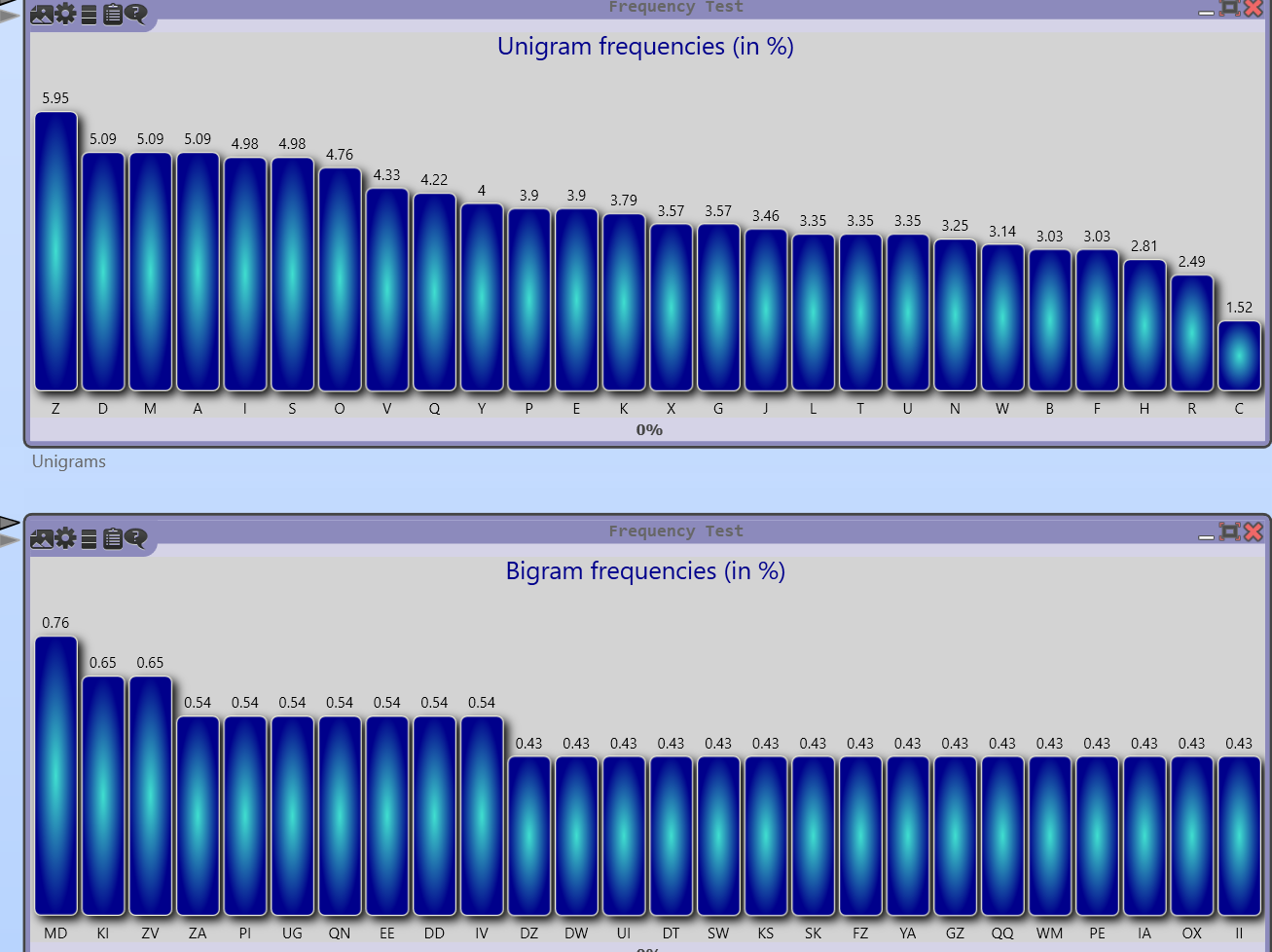
Let’s first have a look at the letter and letter pair frequencies (determined with the software CrypTool):
The distribution is quite flat. This suggests that no simple letter substitution was used. A transposition cipher does not fit either. A Vigenère cipher is at least unlikely.
What, then, could it be? My blog readers have suggested, among other things:
- One-Time-Pad: This method was not too widely used during World War II.
- Enigma: Spies did not use enigmas, as one would have been too conspicuous. However, an Abwehr operative might have used an Abwehr enigma (one existed).
- Book cipher: Such a cipher is usually written down with numbers. For example, 12345 can stand for the 45th letter on page 123. But that does not fit here.
- Codebook: There are codebooks that contain code words consisting of five letters, but in this case there are usually shorter groups of letters at the end of the messages. This indicates that the encryption was not done word by word, but letter by letter. A codebook is therefore unlikely.
In 2017, I gave a talk at the Euro HCC (now known as HistoCrypt) on German spy ciphers in WWII. There are slides on it here. I have listed other methods in the paper accompanying the talk:
It is noticeable that Nazi spies used many different methods (the list is certainly not nearly complete). Most of these methods were quite simple and not overly secure. Presumably, the crypto specialists in charge thought up different ciphers for different spies, taking into account the operational environment and the skills of the person in question.
My guess, therefore, is that Köhler also encrypted using a rather simple but reasonably workable method. Of the procedures mentioned in my slides and on the list, most do not fit. However, the ABC method and the method used by Kunsemueller could at least be checked.
Can any reader say more about this cryptological cold case? If so, I would certainly mention this during the podcast interview.
If you want to add a comment, you need to add it to the German version here.
Follow @KlausSchmeh
Further reading: Wie die Briten Jagd auf deutsche Spionage-Mitteilungen machten
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/




Letzte Kommentare