The list of most-frequently used passwords has changed little over the past few years. In 2016, “123456” once again was the most popular one.
Every year in January IT security company Splashdata selects the most popular password of the past year. This procedure is usually little exciting, as “123456” has been the winner many times in a row.
And the winner is …
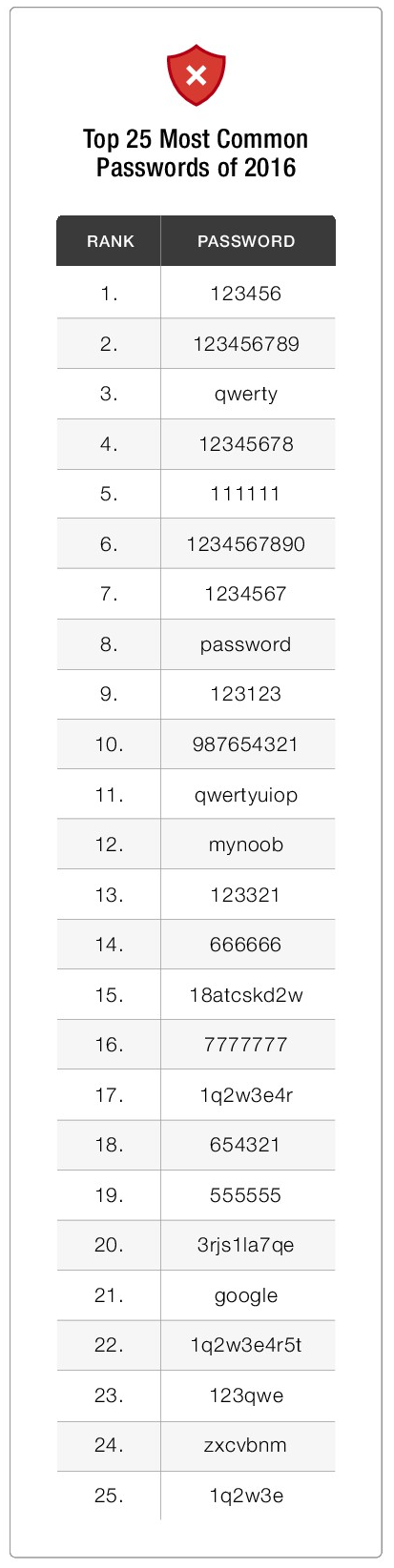
Which password was the most popular of 2016? First of all, this is difficult to say, as Splashdata hasn’t published its usual press release yet. So, I had to look for another source, and I found one. As it turned out, Keeper, a Chicago based company has recently published a password analysis. The most important result is not very surprising: the most popular password of 2016 was “123456”.
As it seems, Keeper took a similar approach as Splashdata in the years before. Its analysis is based on 10 million passwords from data breaches that happened in 2016. Here’s the top 25:
There’s at least one good news: most of the passwords on the list contain one or more non-alphabetical characters. This enlarges the search space. On the other hand, IT users seem to be very reluctant to include capital letters and special characters into their passwords.
According to Keeper CEO Darren Guccione, a few more things jump out:
- The list of most-frequently used passwords has changed little over the past few years. That means that user education and awareness programs have limits.
- Four of the top 10 passwords on the list – and seven of the top 15 – are six characters or shorter.
- The presence of passwords like “1q2w3e4r” and “123qwe” indicates that some users attempt to use unpredictable patterns to secure passwords, but their efforts are weak at best.
Obviously, there is an easy way to avoid all these popular passwords: IT systems should only accept passwords that have at least eight characters and that contain capital letters as well as special signs.
It’s even worse than it seems
It is easy to see that things are even worse than the top 25 list indicates. Many popular passwords don’t even show up in such a ranking. Especially, many users tend to use their names as passwords. This bad habit has inspired episode 5 of my cartoon series Chief Security Officer:
In addition, the company name and other personal data are often used as passwords. Of course, password cracking programs are aware of this.
There are two passwords on the Keeper list I have no explanation for: “18atcskd2w” and “3rjs1la7qe”. According to Darren Guccione, these are letter sequences created by bots and used over and over when they set up dummy accounts on public email services for spam and phishing attacks. If this explanation is correct, email providers could do everyone a favor by flagging this kind of repetition and reporting the guilty parties. If you have another explanation for these passwords to be so popular, please let me know.
Follow @KlausSchmeh
Further reading: How I almost saved the world in a Cryptology escape room
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/




Kommentare (13)