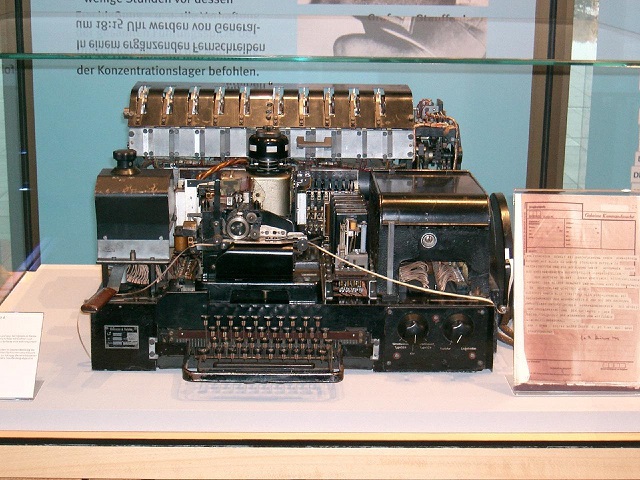
The Siemens & Halske Geheimschreiber (T-52) was the second-most im portant encryption machine of the Germans in World War II. George Lasry has recently published a few computer-based attacks on this device.
The Siemens & Halske T52, also known as “Geheimschreiber”, is a teleprinter encryption system that was used by the Germans during the Second World War. The British codebreakers in Bletchley Park codenamed it “Sturgeon”.
The British could break some of the Geheimschreiber messages, but their focus lay on the Enigma and the Lorenz cipher machine (another German teletype encrypter). The Swedish were successful, too. The reconstruction and solution of the Geheimschreiber by mathematics professor Arne Beurling in 1940 is well known and is considered one of the most impressive codebreaking achievements in history.
The Geheimschreiber, which was mainly used by the German air force, the navy and the foreign office, implemented a combination of addition and transposition cipher. In later models (T52d, T52e), the wheels stepped irregularly.
Bletchley Park and Sweden were able to decipher Geheimschreiber traffic until 1943. They profitted from operator mistakes, such as sending large numbers of messages with the same key. As encryption procedures were improved and with the introduction of the T52d, the Geheimschreiber traffic could not be broken any more.
In a report from 1944, every attempt to solve the T52d is considered to be “completely hopeless”. From 1944 on, no new attacks on the Geheimschreiber became known for decades. While in recent years several codebreakers successfully cryptanalyzed the Enigma using computer technology and new algorithms, nobody seemed to be interested in attacking the Geheimschreiber.
George Lasry’s Geheimschreiber project
The situation changed when Israeli codebreaker George Lasry (the picture shows him with crypto legend Whitfield Diffie) …
… came into play. George is the world’s leading expert in breaking historical encryption methods when the method is known (i.e., when the goal is to find the key). He has published a number of great papers about breaking messages encrypted with the Enigma, Hagelin machines, the Double Column Transposition, ADFGVX and other systems. In his 2016 presentation on unsolved historical cipher problems, George included the problem of reading T52d traffic as one of the top 10.
George started his work by examining the early Geheimschreiber models (T52a/b, T52c, and T52ca). He developed several new statistical attacks to recover the key and the plaintext from the ciphertext. The highlight of this first project part was when he obtained, with the help of Anders Wik and Frode Weierud, a few original cryptograms (from 1941 and 1942). Due to the low quality of the teleprinter print-outs, he initially had some trouble to read them, but after a while he was able to recover the keys and decipher several messages encrypted with the T52a/b model. The subjects of the messages vary from B-Dienst instructions sent to a listening post in Kirkenes (Northern Norway) to mundane administrative matters, such as a planned vacation of a Dr. Colemann, a weather forecast officer in Bergen.
During this process, George and his fellows were able to learn more about the exact mechanisms of the T52 (for example, they had thought that encipherment occurs first, then the wheels move – it turned out that the opposite is the case), and of German keying procedures.
Unfortunately, George’s statistical attacks do not apply to models with irregular wheel stepping (T52d, T52e). Brute-force is not an option due to the size of the keyspace (there are 10^27 = 2^90 keys). In the second part of the project he therefore developed a known-plaintext (“crib”) attack on the Geheimschreiber. George started with a method that could be applied to early Geheimschreiber models, and it worked very well. With this method, he recovered the key from cryptograms (for which the plaintext was also given) that appear in a Swedish TV documentary (minute 23:00).
Taking advantage of a very subtle weakness in the logic that controls the movement of the wheels, George was able to extend his known-plaintext attack to the T52d (and to some extent, the T52e, which is even more secure). Unfortunately, he does not have any original T52d cryptograms he can apply his method on. Says George: “While this attack requires substantial computing power, it is definitely a practical one, and for the first time since WW2, we can say that the T52d problem is not hopeless anymore.”
George recently presented his results on Geheimschreiber cryptanalysis at Histocrypt in Uppsala, Sweden, as part of the special session about Arne Beurling. Here are his slides for download.
An unsolved cryptogram
George has provided me a brochure issued by the Swedish FRA on its WW2 achievements (there is an English and a Swedish version). It contains an example of a Geheimschreiber cryptogram, …
… George is unable to solve. He said: “Maybe a blog reader would like to try his luck.”
Follow @KlausSchmeh
Further reading: My visit to Poznań, where the breaking of the Enigma began
Linkedin: https://www.linkedin.com/groups/13501820
Facebook: https://www.facebook.com/groups/763282653806483/








Kommentare (4)