
Suchergebnisse für „25“
Three months ago, I presented a terminology for codes and nomenclators, based on a workshop that took place at the HistoCrypt conference. After having received some interesting feedback, I can now provide an update.
The Vernam cipher is mentioned in dozens of cryptography books. It is simple and more secure than most other basic encryption methods. Can you solve the three Vernam challenges I am going to introduce today?
Can a reader decipher this encrypted diary page I found on the internet? I don’t know by whom and when it was written, but I’m sure that it can be solved.
At the 44CON, a London-based hacker conference, I gave a talk about Post-Quantum cryptography. Among other things, I explained the GGH algorithm – using snail terminology.
In 1926 a US newspaper published a series of crime stories that involved encrypted messages. Here are four of them. Can you break them?
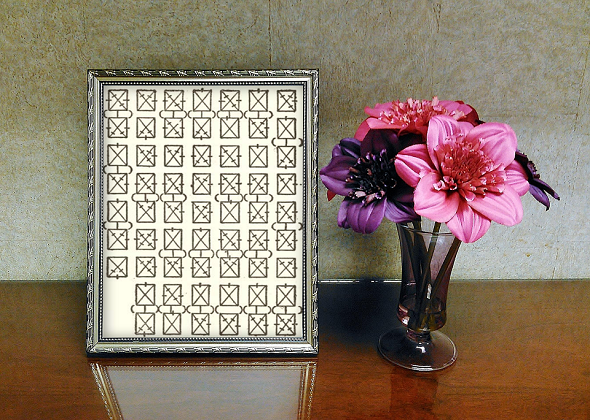
Craig Bauer, mathematics professor and crypto history expert, lets his students solve old ciphertexts as homework. Here are three especially interesting cryptograms Craig’s students have to break.
Nathaniel Bar-Jonah (1957-2008) was a felon convicted of kidnapping and sexual assault. According to a book, he left behind an encrypted note that has never been solved.
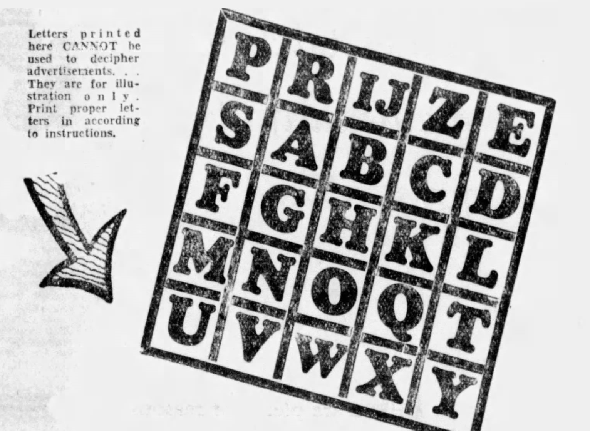
In the 1930s, a US newspaper introduced an interesting way of making their advertisements more attractive. They published two Playfair cryptograms, the keys of which were hidden in an ad on the same page.
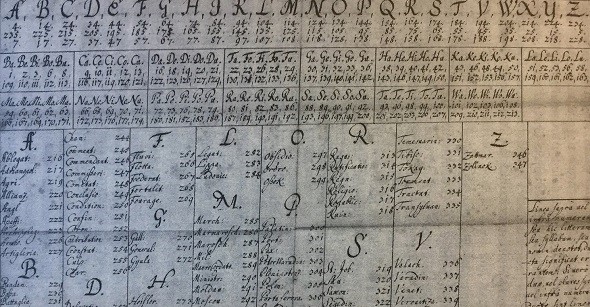
In his ground-breaking book “The Codebreakers”, David Kahn mentions a manual encryption method from 1929 he calls “ingenious”. However, neither Kahn’s book nor any other literature source I know gives a description of this method.
US codebreaker Jim Gillogly broke over 1,000 transposition cryptograms created by IRA activists in the 1920s. Only one of these messages remained unsolved. Can a reader break it?

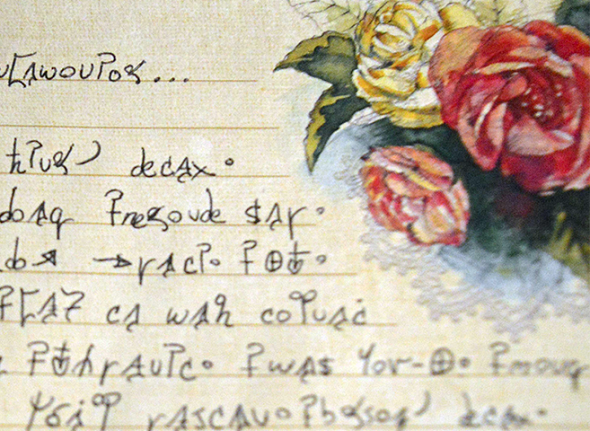






Letzte Kommentare